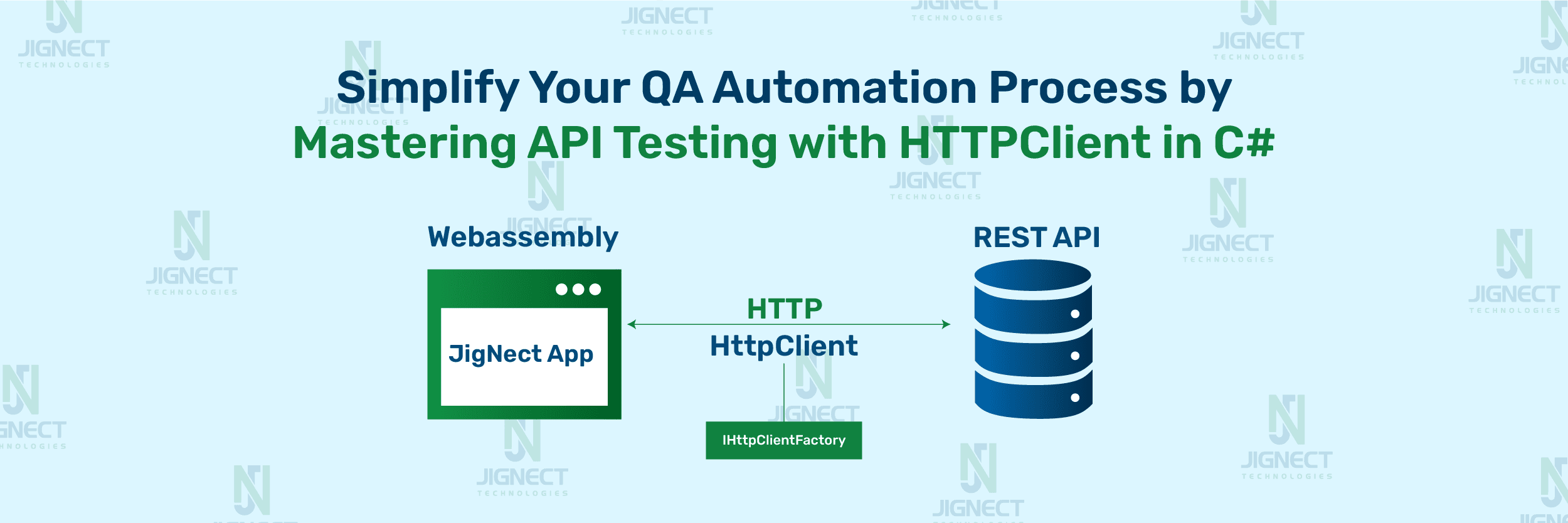
Top-notch Security Testing Services
Security testing services aim to detect, analyze, and assist in remediating vulnerabilities that allow unauthorized access to data, applications, and IT infrastructure. Regular assessments of IT assets and security policies and procedures assist companies in avoiding expensive cyber incidents and compliance violations.
At JigNect, we understand the critical importance of security in today’s digital landscape. As a trusted provider of quality assurance (QA) services, we recognize the significance of safeguarding sensitive information and protecting our clients’ digital assets. Through robust security testing practices, we uphold the highest standards of security and integrity.
Security Testing Services We Provide
Vulnerability Scanning
Security Scanning
Penetration Testing
Risk Assessment
Security Auditing
Ethical Hacking
What We Can Test ?
Web Application
Mobile Application
Desktop Application
IoT
Major Tools we use for Security Testing
These are the tools our team uses for security test planning and testing the most frequently. If you prefer other solutions, just let us know.
Documentation Provided By Us
Risk Assessment Report
A risk assessment report identifies potential security risks, threats, and vulnerabilities that were identified during the testing process. It includes an analysis of the likelihood and impact of each risk, as well as recommendations for mitigating those risks.
Vulnerability Assessment Report
This report provides a detailed analysis of the vulnerabilities discovered during the vulnerability assessment phase of the security testing. It includes information about each vulnerability, such as its severity, impact, and remediation recommendations.
Penetration Testing Report
The penetration testing report summarizes the findings from the simulated cyber attacks conducted during the penetration testing phase. It details the techniques used, the vulnerabilities exploited, and the outcomes of the attacks, along with recommendations for strengthening defenses.
Authentication and Authorization Evaluation Report
This report evaluates the effectiveness of authentication mechanisms (e.g., password policies, multi-factor authentication) and authorization controls (e.g., role-based access controls) in controlling access to resources. It highlights any weaknesses or vulnerabilities in these mechanisms and provides recommendations for improvement.
Data Encryption and Protection Assessment Report
This report assesses how sensitive data is handled, stored, and transmitted within the system. It evaluates encryption protocols, data masking techniques, and data storage practices to ensure that sensitive information is adequately protected from unauthorized access and disclosure.
Security Configuration Review Report
The security configuration review report examines the security configurations of the underlying infrastructure, servers, databases, and third-party components used by the system. It identifies misconfigurations, weak security settings, and unnecessary services or privileges that could expose the system to security risks.
Compliance Assessment Report
This report validates compliance with industry standards, regulatory requirements, and security best practices. It ensures that the system meets the requirements of relevant regulations such as GDPR, PCI DSS, HIPAA, and others.
Step-by-Step Approach to Security Testing Services
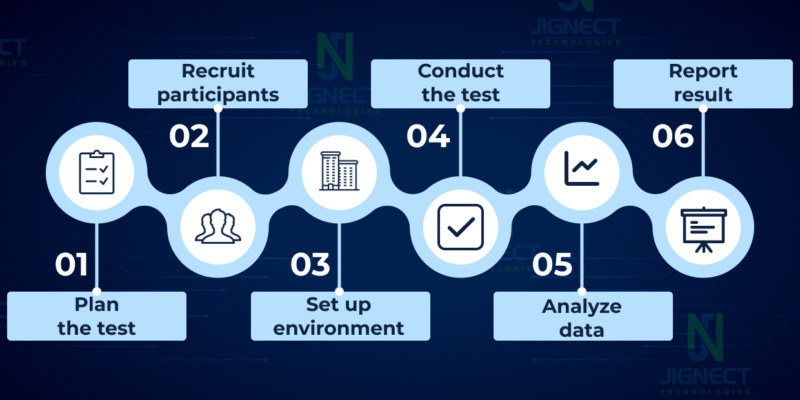
Gather Requirements
Understand the security requirements of the system or application under test. This includes identifying sensitive data, regulatory compliance needs, and any specific security standards or guidelines that need to be followed.
Identify Assets and Threats
Identify the assets (e.g., data, systems, infrastructure) that need to be protected and potential threats (e.g., unauthorized access, data breaches, denial of service attacks) that could compromise their security.
Define Test Objectives
Based on the requirements and identified threats, define clear objectives for the security testing effort. These objectives will guide the selection of testing techniques and methodologies.
Select Security Testing Techniques
Choose appropriate security testing techniques based on the objectives and requirements. Common techniques include vulnerability assessment, penetration testing, security configuration review, authentication and authorization testing, and data encryption testing.
Create Test Plan
Develop a detailed test plan that outlines the scope, approach, methodologies, tools, and resources for the security testing effort. Define test scenarios, test cases, and success criteria for each type of security testing to be performed.
Prepare Test Environment
Set up a dedicated test environment that closely mirrors the production environment but is isolated from it to prevent any impact on live systems. Ensure that necessary security tools, testing frameworks, and resources are available in the test environment.
Perform Vulnerability Assessment
Conduct a vulnerability assessment to identify potential security vulnerabilities and weaknesses in the system or application. Use automated scanning tools and manual inspection techniques to assess the security posture and identify common vulnerabilities such as XSS, SQL injection, CSRF, and misconfigurations.
Conduct Penetration Testing
Perform penetration testing to simulate real-world cyber attacks and assess the resilience of the system or application's defenses. Ethical hackers attempt to exploit identified vulnerabilities and entry points to gain unauthorized access or compromise sensitive data.
Evaluate Authentication and Authorization
Evaluate the effectiveness of authentication mechanisms (e.g., password policies, MFA, session management) and authorization controls (e.g., RBAC) in controlling access to resources and functionalities. Test for weaknesses in authentication and authorization mechanisms that could lead to unauthorized access.
Assess Data Encryption and Protection
Assess how sensitive data is handled, stored, and transmitted within the system or application. Evaluate encryption protocols, data masking techniques, secure storage mechanisms, and data deletion processes to ensure that sensitive information is adequately protected from unauthorized access and disclosure.
Review Security Configurations
Review the security configurations of the underlying infrastructure, servers, databases, and third-party components used by the system or application. Identify and mitigate misconfigurations, weak security settings, and unnecessary services or privileges that could expose the system to security risks.
Validate Compliance Requirements
Validate compliance with industry standards, regulatory requirements, and security best practices. Ensure that the system or application meets the requirements of relevant regulations such as GDPR, PCI DSS, HIPAA, and others.
Document Findings and Remediate Issues
Document all findings, including identified vulnerabilities, weaknesses, and areas of non-compliance. Prioritize issues based on severity and impact, and work with development teams to remediate them promptly.
Retest and Validate Fixes
After fixes have been implemented, retest the system or application to validate that security issues have been addressed effectively. Ensure that all identified vulnerabilities have been patched and that the system remains resilient against potential security threats.
Report Results and Provide Recommendations
Prepare a comprehensive report summarizing the security testing process, findings, remediation efforts, and recommendations for improving the security posture of the system or application. Share the report with stakeholders and collaborate on any further actions required to enhance security.
Gather Requirements
Understand the security requirements of the system or application under test. This includes identifying sensitive data, regulatory compliance needs, and any specific security standards or guidelines that need to be followed.
Identify Assets and Threats
Identify the assets (e.g., data, systems, infrastructure) that need to be protected and potential threats (e.g., unauthorized access, data breaches, denial of service attacks) that could compromise their security.
Define Test Objectives
Based on the requirements and identified threats, define clear objectives for the security testing effort. These objectives will guide the selection of testing techniques and methodologies.
Select Security Testing Techniques
Choose appropriate security testing techniques based on the objectives and requirements. Common techniques include vulnerability assessment, penetration testing, security configuration review, authentication and authorization testing, and data encryption testing.
Create Test Plan
Develop a detailed test plan that outlines the scope, approach, methodologies, tools, and resources for the security testing effort. Define test scenarios, test cases, and success criteria for each type of security testing to be performed.
Prepare Test Environment
Set up a dedicated test environment that closely mirrors the production environment but is isolated from it to prevent any impact on live systems. Ensure that necessary security tools, testing frameworks, and resources are available in the test environment.
Perform Vulnerability Assessment
Conduct a vulnerability assessment to identify potential security vulnerabilities and weaknesses in the system or application. Use automated scanning tools and manual inspection techniques to assess the security posture and identify common vulnerabilities such as XSS, SQL injection, CSRF, and misconfigurations.
Conduct Penetration Testing
Perform penetration testing to simulate real-world cyber attacks and assess the resilience of the system or application's defenses. Ethical hackers attempt to exploit identified vulnerabilities and entry points to gain unauthorized access or compromise sensitive data.
Evaluate Authentication and Authorization
Evaluate the effectiveness of authentication mechanisms (e.g., password policies, MFA, session management) and authorization controls (e.g., RBAC) in controlling access to resources and functionalities. Test for weaknesses in authentication and authorization mechanisms that could lead to unauthorized access.
Assess Data Encryption and Protection
Assess how sensitive data is handled, stored, and transmitted within the system or application. Evaluate encryption protocols, data masking techniques, secure storage mechanisms, and data deletion processes to ensure that sensitive information is adequately protected from unauthorized access and disclosure.
Review Security Configurations
Review the security configurations of the underlying infrastructure, servers, databases, and third-party components used by the system or application. Identify and mitigate misconfigurations, weak security settings, and unnecessary services or privileges that could expose the system to security risks.
Validate Compliance Requirements
Validate compliance with industry standards, regulatory requirements, and security best practices. Ensure that the system or application meets the requirements of relevant regulations such as GDPR, PCI DSS, HIPAA, and others.
Document Findings and Remediate Issues
Document all findings, including identified vulnerabilities, weaknesses, and areas of non-compliance. Prioritize issues based on severity and impact, and work with development teams to remediate them promptly.
Retest and Validate Fixes
After fixes have been implemented, retest the system or application to validate that security issues have been addressed effectively. Ensure that all identified vulnerabilities have been patched and that the system remains resilient against potential security threats.
Report Results and Provide Recommendations
Prepare a comprehensive report summarizing the security testing process, findings, remediation efforts, and recommendations for improving the security posture of the system or application. Share the report with stakeholders and collaborate on any further actions required to enhance security.
Benefits of Security Testing Service
By utilizing JigNect Technologies’ automated testing service, you can expect to gain numerous advantages. Through our expertise in the domain, we help you unlock the following benefits for your business:
Improved Quality
Through thorough testing of the application or system, functional testing helps pinpoint and resolve any defects, guaranteeing that the application or system fulfills its functional specifications. This improves the software’s overall quality.
Increased User Satisfaction
Functional testing increases user satisfaction and reduces the risk of user frustration or confusion by ensuring that a software product functions accurately as expected. This can lead to increased customer loyalty and positive feedback.
Enhanced Reliability
By thoroughly testing the application or system, functional testing helps increase its reliability and reduce the risk of failure. This helps ensure that the application or system performs as expected and meets the needs of its users.
Increased Confidence
By thoroughly testing the application or system, functional testing provides confidence in its ability to meet its functional requirements and perform as expected. This helps ensure that the application or system is ready for deployment and use by its users
Early Defect Detection
Functional testing reduces the expenses associated with bug fixes and minimizes the likelihood of encountering problems during the later stages of development by detecting defects early on in the process. This helps guarantee that the application or system will be delivered on time and within budget.