Think of your web app as the front door to your digital business. Your app is always “live,” processing logins, transactions, and private information – and this is all done in an online environment. Attackers are lurking nearby, waiting for a vulnerability to slip in through. Security threats are not slowing down. In fact, they become smarter, faster, and more complex with every new feature. As teams rush to deliver updates and enhancements, security can sometimes be neglected. The truth is, users expect security, even if they never ask for it.
This blog is going to discuss web application security testing in depth. You will get a real-life explanation of why testing is important, how common vulnerabilities like SQL injection and cross-site scripting work, and what can happen when they are not tested for. We will also compare manual testing with automated testing, identify who does what, and how to build security into your development process from the beginning. If you have any role from coding, testing to leading a product team, you will leave with the knowledge and tools needed to ensure your app is secure, safe, and reliable. Let’s go!
- Introduction to Web App Security
- Why Web Application Security Testing Matters ?
- Common attack types (XSS, SQLi, CSRF)
- Who Performs Web Application Security Testing
- How Web App Security Testing is being Performed ?
- Security Testing Types
- Common Web Application Vulnerabilities
- Reporting and Remediation: Turning Security Findings into Action
- Best Practices: Incorporating Security into Your Web Applications
- 1. Adopt a Shift-Left Security Mindset
- 2. Adhere to Secure Coding Practices
- 3. Enact Strong Authentication and Authorization
- 4. Secure APIs and Third-Party Integrations
- 5. Perform Periodic Audits and Updates
- 6. Conduct Threat Modeling
- 7. Defend Against Common Vulnerabilities
- 8. Encrypt Data at Rest and in Transit
- 9. Test and Monitor Periodically
- Security Testing Standards & Guidelines: A Simple Guide to Keeping Your App Safe
- Conclusion
Introduction to Web App Security
If you have ever done some shopping online, accessed your bank balance via your phone, or simply looked at social media, then you have used the applications of the web. Such applications are now an integral part of everyday life that we do not even give it much thought. Yet, behind each problem-free log in and trouble-free transaction, there lies an invisible realm of security threats, and an army of individuals who labor tirelessly to keep your data secure.
Why Web Application Security is Not Only For Geeks
Web application security is not just an IT buzzword. It is an issue for everyone, right from the CEO all the way down to the end user. In essence, web app security is about ensuring that data that you post online or offline, whether it is your e-mail address, your credit card, or your health record remains personal and safe.
Let’s phrase it differently: suppose you are in charge of a small bakery, and you just introduced an online ordering platform. You would not want somebody to break into your kitchen and mess with your recipes, right? The same goes for your website. If you do not secure the virtual doors, someone may break in and create mayhem.
The Real-World Cost of Getting It Wrong
The prime example of things that can go terribly wrong is TalkTalk’s UK breach.
In 2015, hackers found a flaw in an old part of TalkTalk’s website. With it, they accessed the personal details of over 150,000 customers names, addresses, bank details. The aftermath: TalkTalk lost millions of pounds, incurred regulatory sanctions, and had its reputation plummet. All because of one, neglected vulnerability.
Security Is a Moving Target
Here’s the reality: the dangers to web applications are not static. There are always new tricks being concocted by hackers, and the technology landscape keeps evolving. What was secure five years ago would have holes in it today. So, web application security is not a project that we do once and are done with it. It’s an ongoing effort.
And it’s not all about the technical mistakes, either. Human errors like “password123” or simply neglecting to install patches can let attackers in just as quickly as an application flaw.
The Chain Is Only as Strong as Its Weakest Link
It’s possible, even common, for the weakest link to lie somewhere other than in your own application.
Consider the British Airways incident back in 2018. Attackers didn’t compromise the airline’s corporate website. Instead, they targeted an exploit in an outside script deployed on the checkout page. That small crack was all they required to steal customer payment data from hundreds of thousands of transactions.
The moral of the story? Web application security is about examining the complete environment, not just your own domain.
Why Web Application Security Testing Matters ?
Let’s suppose you just constructed an exquisite new home. Would you move in before checking the door and window locks? Most likely not. The reasoning is the same when it comes to web applications. Before inviting users in, you must ensure everything is secure.
The Dark Side of Code
Each web application is composed of thousands, sometimes millions of lines of code. Even professional developers are prone to errors, and attackers specialize in uncovering those small mistakes. That’s where security testing takes over. It’s akin to seeking the services of an expert to examine your home, searching for any vulnerability that an intruder can use.
What If You Don’t Test Security?
Missing out on security testing is similar to walking outside to your car in a public parking lot with the doors unlocked. Eventually, someone is going to open the door. The ramifications can be dire:
- Data Breaches: Sensitive data can fall into the wrong hands.
- Financial Loss: Financial losses may occur directly from theft, or indirectly through lost business and fines. Companies have an obligation to secure customer data, and failing to do so may lead to lawsuits and financial penalties.
- Reputation Loss: When word spreads that your website is unsafe, the customers are unlikely to want to go back.
A classic example is the TalkTalk hack discussed above. TalkTalk could have picked up the vulnerability with just a few security checks. Instead, they paid the cost.
What Does Security Testing Actually Involve?
Security testing is not about firing out a high-end tool and walking away. It’s an even balance of automated scans and manual investigation. This is what it commonly encompasses:
- Map Out the Application: Tracking down where users can connect with your website.
- Permissions Checking: Ensuring that users cannot get to things they shouldn’t.
- Attempting to Break In: Ethical hackers, also referred to as “pen testers,” attempt to take advantage of weaknesses, similar to attackers.
- Validating Inputs: Preventing anything users can type in, such as searches or comments from being exploited to inject harmful code.
- Reviewing Authentication: Ensuring that logon systems are secure and sessions cannot be hijacked.
Security Testing Is a Habit, Not an Occasional Exercise
It’s all too easy to assume you can just test it once and forget. But each time you add an update, new feature, or new infrastructure, new vulnerabilities can emerge. That’s why the best teams embed security testing as part of their routine, part of their workflow, and not an afterthought.
A Close Call: The Importance of Regular Testing
One popular online store recently found an open API endpoint that they didn’t realize existed because of an update. Had attackers discovered it, they would have exposed customer orders and personal information. Thankfully, because they were performing automated security checks that they do regularly, they caught the problem before it ever manifested. That’s the value of proactive testing.
Common attack types (XSS, SQLi, CSRF)
1. Cross-Site Scripting (XSS): When Websites Turn Against You
An attacker learns to place malicious scripts on pages that other users visit. These scripts typically execute within the victim’s browser, and the attacker can use them to steal cookies, hijack sessions, or deface the site.
How it works?
- The website does not adequately sanitize user input.
- An attacker makes a post or message with an embedded script.
- The script automatically runs when another user visits the page.
Real-World Example
The British Airways hack compromise involved attackers inserting malicious data into an external script. When each customer would input their financial information, the script would secretly transmit that data to the hackers. It’s an all-too-familiar display of XSS.
2. SQL Injection (SQLi): Hacking the Database
SQL injection is an oldie but goodie in the hacker’s playbook. It occurs when an attacker places specially created input into the form field, which makes the application execute unknown commands against the database.
How it works?
- The login form does not verify anything that users input.
- An attacker inputs SQL code where the username or password would go.
- The database runs the code, revealing or changing sensitive information.
Real-World Example
The TalkTalk hack occurred as a consequence of SQL injection. Hackers utilized it to gain entry into customer data, simply because the application failed to validate input.
3. Cross-Site Request Forgery (CSRF): Fooling Users into Acting
CSRF is more insidious. It convinces users to do things they didn’t mean to, such as resetting their password or sending money, just by visiting an evil website while still logged into another service.
How it works?
- The victim is already signed in to a website (e.g., their bank).
- The attacker forwards them with a link or embeds an invisible request in an email or webpage.
- Unbeknownst to the victim, the victim’s browser makes an automated request to the bank, conducting an act as though done by the victim.
Real-World Example
Suppose that a customer is logged into their bank account. He browses an untrustworthy website, which quietly posts a form to initiate an order for transferring money out of their account. If the bank’s website does not verify the source where the request is initiated, the money is transferred without asking questions.
Who Performs Web Application Security Testing
Web application security testing is a collaborative effort that involves a variety of specialized roles. Each group brings unique skills, perspectives, and tools to the table, ensuring comprehensive coverage against a wide spectrum of threats. Here’s a breakdown of the key players involved in web application security testing:
Internal Security Teams
Internal security teams are dedicated professionals working within an organization. Their deep understanding of the company’s infrastructure, applications, and business processes allows them to identify vulnerabilities that are specific to the organization’s environment. These teams often:
- Develop and implement security policies and procedures.
- Conduct regular vulnerability assessments and penetration tests.
- Respond quickly to incidents and emerging threats.
- Collaborate closely with development and IT teams to remediate issues.
Having an internal team ensures ongoing vigilance and a proactive approach to web application security.
QA Engineers with Security Knowledge
Quality Assurance (QA) engineers traditionally focus on functional and performance testing, but those with security expertise add immense value to the development lifecycle. Security-aware QA engineers:
- Integrate security test cases into standard QA processes.
- Identify flaws in business logic, authentication, and authorization.
- Use both manual and automated tools to uncover vulnerabilities early.
- Advocate for secure coding practices and “shift-left” security.
By embedding security into QA, organizations can catch issues before they reach production, saving time and resources.
Ethical Hackers and Penetration Testers
Ethical hackers, also known as “white-hat” hackers, and penetration testers simulate real-world attacks to uncover vulnerabilities before malicious actors do. Their approach includes:
- Using advanced tools and creative techniques to bypass security controls.
- Performing both automated testing and manual testing to mimic attacker behavior.
- Providing detailed reports with proof-of-concept exploits and remediation advice.
- Staying updated with the latest threat landscapes and attack vectors.
Their outsider perspective and adversarial mindset are crucial for identifying weaknesses that may be overlooked by internal teams.
Third-Party Security Firms
Many organizations engage third-party security firms to conduct independent assessments. These firms offer:
- Objective, unbiased evaluations of web application security.
- Access to a broad range of expertise and specialized testing tools.
- Comprehensive reports aligned with industry standards (e.g., OWASP, NIST).
- Validation for compliance and regulatory requirements.
Third-party assessments add credibility and often reveal hidden issues, making them a valuable part of a robust security strategy.
Bug Bounty Hunters
Bug bounty hunters are independent security researchers who participate in public or private bug bounty programs. They:
- Search for vulnerabilities in exchange for monetary rewards or recognition.
- Bring diverse skills and perspectives from around the globe.
- Often discover unique or previously unknown vulnerabilities.
- Help organizations crowdsource security testing via many methods beyond traditional.
Bug bounty programs harness the collective intelligence of the security community, providing an additional layer of defense.
Each of these groups plays a vital role in securing web applications. By leveraging their combined expertise, organizations can build resilient, secure, and trustworthy web platforms.
How Web App Security Testing is being Performed ?
Web app security testing is a systematic, stages of effort, process for recognizing and addressing vulnerabilities.
It ultimately begins with scoping and collecting information on the app. Then starts the standard acquisition of information, with automated scans using scanning tools like Burp Suite, to identify common issues like injection vulnerabilities or misconfigurations. Experts than conduct their manual review of the code, looking for the more complex bugs found in logic errors. Penetration tests are done as simulacra of hackers testing the effectiveness of the entire security of the web application. The action plan outlining all issues that need to be fixed is reported in detail, with ranked levels of importance in some cases. The teams then work collaboratively on the critical fixes, maybe to introduce secure headers or change input validation.
Finally, they all must retest properly to ensure there are no outstanding issues, and further maintain the integrity of the security of the web application.
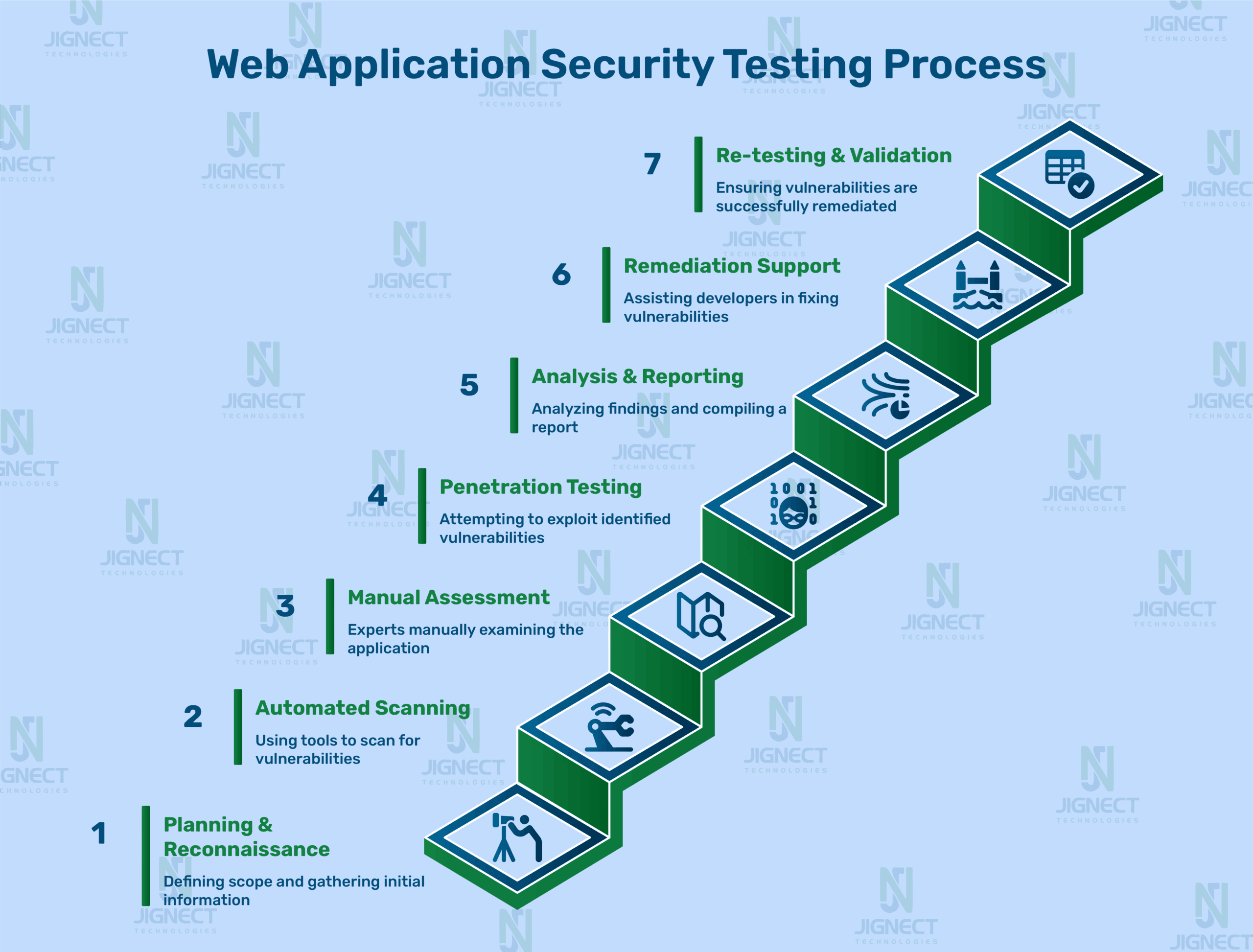
Aside from the formalized steps, web app security testing is best considered as a team sport that applies, incorporates and adapts cutting-edge techniques, test models and pre-emptive methods that are constantly evolving to assess evolving threats. The team can use threat intelligence feeds to track evolving attack patterns, or do red team exercises to validate their assumptions of security posture, or employ chaos engineering to test the application’s ability to perform in unforeseen conditions. Instead of just the developers and security teams working collaboratively, the executive level can also be engaged in security as part of the larger DevOps workflow strategy, with continuous integration sweeps of checking software security with founder or CTO signing off at the end; while enabling an AI-driven testing tools to analyze the software for multiple, niche vulnerabilities that manual testing may miss.
Ultimately by implementing this whole-of-business approach, the goal is to achieve not just security for the organization, but also create a security-first mindset throughout the organization.
Security Testing Types
Security testing isn’t one-size-fits-all. What works for one company might fall completely flat for another. That’s why we break it into types-so you can mix and match based on how your app works, what data it touches, and honestly, how paranoid you are (or should be).
Manual Testing
There’s still a lot of value in a human just poking around, trying things out, clicking through weird edge cases. Automated tools are great, but they don’t have intuition, creativity, or that “wait, what if I…” mindset. Manual testers can spot subtle flaws in logic, workflow, and user experience that machines simply overlook.
Business Logic Testing
- Focuses on how the app behaves, not just the code.
- Testers try to misuse features in ways that still technically “follow the rules.”
- Example? Maybe a coupon code meant for new users works for returning ones. That logic has gone rogue.
Business logic bugs are some of the hardest to spot and fix. They’re not about “bad code” but about “unexpected consequences.” Imagine a workflow where a refund can be requested twice, or where a user can escalate privileges by chaining together harmless actions. These issues often require a deep understanding of the business and the app’s intended flow. Automated tools rarely catch these because they don’t understand intent or context-their job is to look for patterns.
Authentication and Authorization Testing
- Verifies who can access what-and when.
- Tries things like bypassing login, messing with session tokens, or accessing admin pages as a normal user.
This is where testers get creative: Can you change a user ID in the URL and see someone else’s data? Can you replay an expired session token? Can you access features meant for admins by tweaking a cookie or HTTP header? These are classic “broken access control” and “broken authentication” issues, and they’re among the most common real-world vulnerabilities. Manual testers often uncover these by simply thinking, “What if I try this as a different user?”
Penetration Testing
- Ethical hackers simulate real-world attacks.
- Goes beyond checklists-testers chain vulnerabilities, try social engineering, and look for creative exploits.
Pen testing is like a dress rehearsal for a real attack. Testers try everything from SQL injection to chaining minor bugs into a major breach. They’ll also look at your infrastructure, APIs, and even your cloud setup. The value here is in the unpredictability-good pen testers think outside the box and often find things automated tools never would.
Automation Testing
Automation doesn’t replace humans, but it can definitely help. Especially for catching obvious or repetitive issues that you’d rather not spend hours manually checking every release.
Security Scanners (e.g., ZAP, Burp Suite)
- Scans for common vulnerabilities like XSS or SQL injection.
- Helps map out the app to find interesting endpoints.
Security scanners are your first line of defense. They’re great at finding low-hanging fruit: outdated libraries, open ports, misconfigured headers, and the classic OWASP Top 10 issues (think XSS, SQLi, CSRF). They’re fast and efficient, but they have limits-they can’t understand business logic, and they sometimes miss issues that require context. Still, running a scanner regularly is a must.
Static Application Security Testing (SAST)
- Looks at the source code without running it.
- Flags insecure functions, hardcoded secrets, or poor coding patterns.
SAST is like a spell-checker for your codebase. It scans for dangerous functions, hardcoded credentials, and insecure patterns-before your code even runs. Particularly in large teams or open-source projects, this is crucial for identifying problems early. Drawbacks? SAST may produce false positives and is unable to detect problems that only manifest during runtime, such as logical errors or configuration errors.
Dynamic Application Security Testing (DAST)
- Tests the running application.
- Acts more like a hacker would: sending inputs, watching responses.
Your DAST is your “black box” test: it won’t mind about your code, but rather what your application does when probed and tested. It is excellent at identifying real-world vulnerabilities, such as injection flaws, XSS, and misconfigurations. DAST tools emulate attacks and observe how your application reacts to them, making them a must-have for staging and production environments.
Interactive Application Security Testing (IAST)
- Combines SAST and DAST by monitoring the app from the inside while it runs.
- Provides real-time, context-aware vulnerability detection.
IAST tools instrument your app so they can see both the code and the data as it flows through the system. More actionable insights and fewer false positives are the results of this hybrid approach. IAST is particularly helpful in contemporary, dynamic environments where infrastructure and code change frequently. The trade-off? It can add some performance overhead and usually requires more setup.
Software Composition Analysis (SCA)
- Scans open-source and third-party components.
- Identifies vulnerabilities, licensing risks, and outdated dependencies.
Most apps today are built on a mountain of third-party libraries. SCA tools scan your dependencies for known vulnerabilities and compliance issues. They’re essential for avoiding “supply chain” attacks, where a bug in a library you didn’t write becomes your problem.
Secret Scanning
- Finds hardcoded credentials, API keys, and tokens in source code and CI/CD pipelines.
- Prevents accidental leaks before they become breaches.
For sensitive information in your codebase, secret scanning tools are similar to metal detectors. They aid in preventing the embarrassing (and hazardous) disclosure of API keys, passwords, and other secrets that hackers love to discover.
Testing Approaches
Different approaches change how you test-not just what tools you use. It’s a bit like wondering, “How familiar with the system do I need to be before I attempt to find its weaknesses?”
Black Box Testing
- The tester knows nothing about the internals.
- Simulates an outside attacker.
Black box testing is the ultimate outsider perspective. Testers use the app like regular users would, without access to inside documents or source code. This method is great for simulating real-world attacks, but it might cause you to miss some more subtle or deeper issues that aren’t visible to the public eye.
White Box Testing
- Full access to source code, architecture, and logic.
- Can be very thorough.
Source code, documentation, architecture diagrams, the works, the keys to the kingdom, that white box testing provides for testers This enables extensive testing, which is perfect for spotting logical errors and minor bugs. It also takes a lot of time and isn’t always practical unless you’re worried about extremely qualified attackers or insider threats.
Grey Box Testing
- Somewhere in between.
- The tester knows some things, like user roles or general architecture.
Grey box testing is the sweet spot for many teams. Testers get enough info to be effective (like API docs or user roles) but not so much that they lose the attacker’s perspective. This approach balances realism and depth, catching a wide range of issues without requiring total access or working completely in the dark.
Common Web Application Vulnerabilities
Web apps have become an integral part of our life today because people use them for shopping, banking, and connecting with their friends, but, at the same time, they present numerous challenges. Recently, I have become more interested in web security. It’s quite amazing and a bit frightening how many things can go wrong. One miscalculation in your steps can lead to app data breaches or leaks. Let me explain further. Together with my research and other people’s experience, I will explain some practical ideas regarding the six common vulnerabilities outlined in the OWASP Top Ten web application vulnerabilities. So let’s begin.
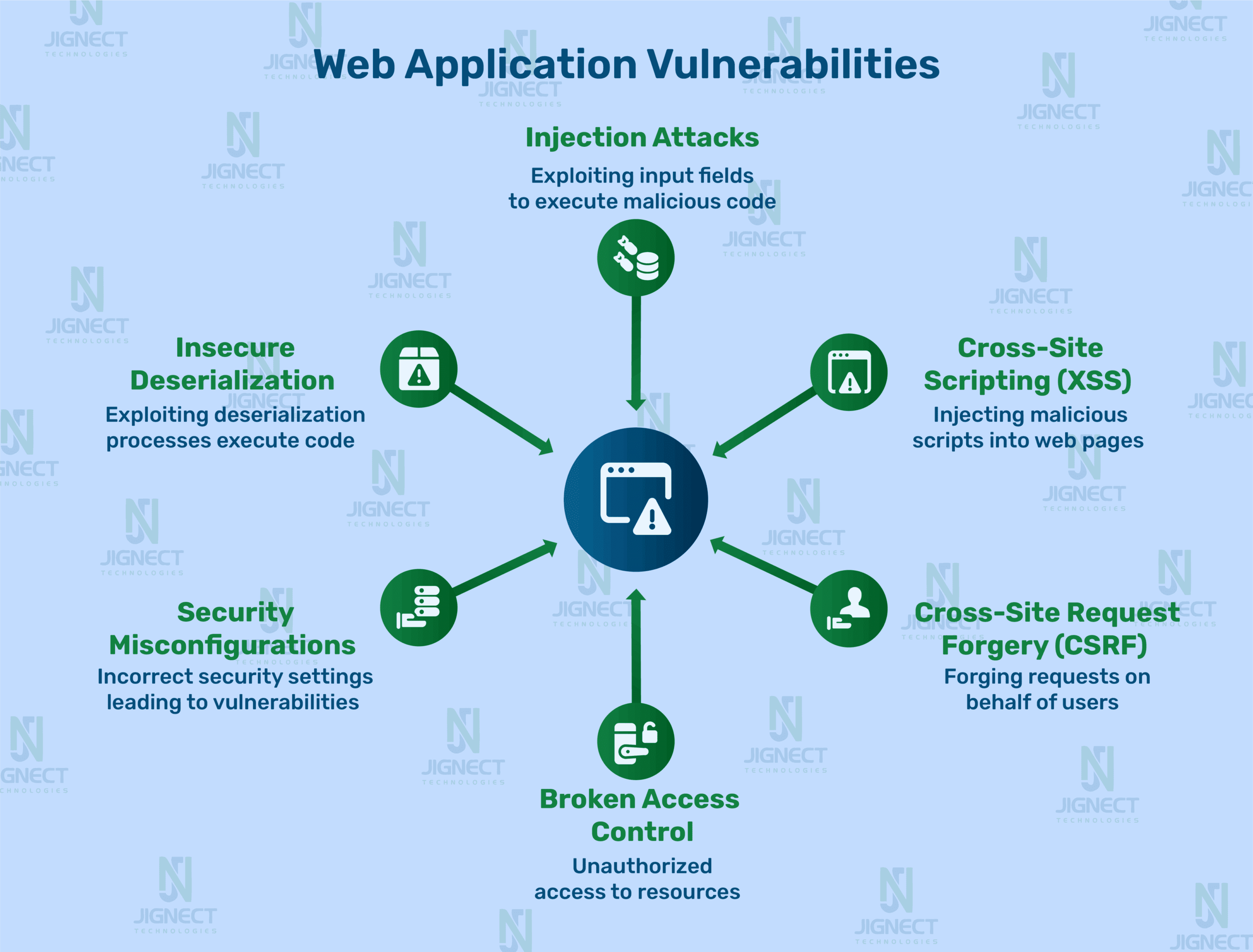
1. Injection Attacks
Injection attacks are like someone slipping a prank into your app’s input fields, turning a harmless form into a disaster. They’re scary because they’re so simple, an attacker just needs to find a weak spot in your input handling, and boom, chaos ensues. I remember reading about a company that lost millions of records because of a poorly handled form field. Let’s look at the ways this can happen.
SQL, Command, and LDAP Injection
What’s Happening?
SQL injection is the classic example. An attacker types something like ' OR '1'='1 into a login form, and if your app doesn’t sanitize inputs, that string can manipulate your database query to bypass authentication. Command injection targets the operating system, letting attackers run arbitrary commands. LDAP injection, less common but still nasty, messes with directory services, potentially exposing user data. I saw a demo once where a single quote in a form field dumped an entire user table, that’s wild.
Fix
- Sanitize Inputs: Always validate and sanitize user inputs. Use prepared statements or parameterized queries for SQL frameworks like Django make this a breeze.
- Escape Special Characters: For LDAP, escape characters like
*or&. For command injection, avoid passing user input to system calls. - Use ORM: Object-Relational Mapping tools can abstract queries, reducing injection risks.
- Least Privilege: Run your database or system with minimal permissions to limit damage.
Code Injection
What’s Happening?
Here the hackers injects the code of PHP or Python which is executable. This happened many times to CMS where attackers upload a script that ran on the server.You can think of a eval() in JavaScript, which is scary.
Fix
- Avoid Eval: Never use functions like
eval()or equivalent in any language. - Input Validation: Strictly validate inputs to ensure they’re not executable code.
- Sandboxing: Run risky operations in a sandboxed environment if you must.
- Code Reviews: Regularly audit your codebase for dangerous functions.
XML Injection
What’s Happening?
XML injection targets apps that parse XML inputs, like APIs or configuration files. Attackers can manipulate XML to alter app behavior or extract data. I read about a case where an attacker injected XML to bypass authentication in a SOAP-based API. It’s less common but still a real threat.
Fix
- Validate XML: Use strict XML parsers and schemas to reject malformed input.
- Sanitize Inputs: Strip out dangerous XML tags or attributes.
- Use Safe Libraries: Libraries like
libxml2can help with secure parsing. - Limit XML Features: Disable external entity processing to prevent XXE attacks.
2. Cross-Site Scripting (XSS)
It is also a type of injection but slightly different. Here the scripts are injected into a trusted website in the form of a script from browser side to another end user.
It’s like setting a concealed snare that activates when a user accesses your webpage. I’ve seen this on old forums where a single malicious comment could hijack sessions. Let’s break down the types.
Stored, Reflected, DOM-based
What’s Happening?
- Stored XSS: The code will run for every user who accesses the page because it is stored like a comment on an active script runner server.
- Reflected XSS: The script is embedded in a URL or form input, affecting users who click a malicious link.
- DOM-based XSS: This one’s trickier, it manipulates the browser’s DOM directly, often without hitting the server. I clicked a demo link once that stole cookies just by tweaking a URL parameter. Not cool.
Fix
- Encode Outputs: Escape HTML characters (like
<and>) before displaying user input. OWASP’s ESAPI is a great library that do this job better. - Content Security Policy (CSP): Implement CSP headers to limit the execution of specific scripts.
- Framework Protections: React or Angular have built-in XSS defenses, but verify your setup.
- Validate Inputs: Filter out dangerous characters server-side, too.
Server-Side XSS
What’s Happening?
Server-side XSS is basically when someone sneaks their nasty little scripts into stuff your server spits out, think error messages, templates, whatever. If your server’s letting any old dynamic crap through without scrubbing it clean, yeah, attackers are gonna pounce. I once saw an app where an error page displayed raw user input, opening the door to scripts.
Fix
- Sanitize Server Output: Ensure all server-generated content is encoded properly.
- Use Safe Templating: Frameworks like Jinja2 or Handlebars have escaping built in, use them.
- Audit Templates: Check your templates for places where user input might sneak in.
- CSP Headers: Again, CSP can limit the damage even if a script slips through.
Client-Side Framework XSS
What’s Happening?
If you think, widely used frameworks like React or Vue are fully protected, but that doesn’t automatically protect you from making mistakes.
For instance, if you start playing around with things like dangerouslySetInnerHTML in React and neglect input sanitization, you’re moving ahead towards trouble.
Yeah, that’s true. I mean, who names something “dangerously”? They’re not exactly being subtle about the risks. I’ve seen developers assume frameworks are bulletproof, only to get burned by edge cases.
Fix
- Avoid Dangerous APIs: Steer clear of
dangerouslySetInnerHTMLor similar unless absolutely necessary. - Sanitize Inputs: Use libraries like DOMPurify to clean user input before rendering.
- Framework Best Practices: Follow your framework’s security guidelines religiously.
- Regular Testing: Use tools like Burp Suite to test for XSS in your app.
3. Cross-Site Request Forgery (CSRF)
CSRF is basically someone sliding into your account and pretending to be you like they just forged your signature on something shady. You didn’t say yes, but now your name’s on it. Sketchy, right?
It tricks a user’s browser into making a request to a site they’re logged into, without their knowledge. I read about a forum post with a hidden <img> tag that triggered account deletions.
How it Works and Prevention
What’s Happening?
CSRF exploits the fact that browsers send cookies automatically with requests. Attackers craft a malicious form or link that submits a request like transferring money from your bank account, while you’re logged in. It’s sneaky because it relies on your existing session.
Fix
- Anti-CSRF Tokens: Toss in these one-of-a-kind, totally random tokens for every user session, and don’t just toss them, double-check them on the server, too. No shortcuts.
- SameSite Cookies: Seriously, just slap that
SameSitelabel on your cookies. That pretty much tells cross-site requests to buzz off. - Explicit Actions: Require re-entering passwords for sensitive actions.
- Header-Based Auth: Use tokens in headers instead of relying solely on cookies.
Token Misuse
What’s Happening?
Even with CSRF tokens, attackers can exploit weak implementations. For example, if tokens are predictable or not tied to a session, attackers can bypass them. I once saw a case where a static token was reused across sessions, It’s a big mistake.
Fix
- Randomize Tokens: Ensure tokens are cryptographically secure and unique per session.
- Session Binding: Tie tokens to a specific user session.
- Short Expiry: Make tokens expire quickly to limit their window of use.
- Validate Origin: Check the
OriginorRefererheader to ensure requests come from your site.
API-Specific CSRF
What’s Happening?
APIs, especially RESTful can be vulnerable to CSRF if they depend on cookie-based authentication. Basically, if your API leans on cookies, someone can just fool a browser into firing off requests on your behalf. I’ve seen this in apps where APIs didn’t enforce proper token checks.
Fix
- Use Bearer Tokens: Prefer token-based authentication (like JWT) in headers over cookies.
- CORS Configuration: Set strict CORS policies to limit which domains can send requests.
- Anti-CSRF Tokens: Apply tokens to API endpoints, not just web forms.
- Disable Cookies for APIs: If possible, avoid cookies for API authentication.
4. Broken Access Control
That’s like tossing your house keys on a public park bench and hoping for the best. When your app flakes out on checking permissions, people end up waltzing into places they’ve got no business being. Seriously, it’s a recipe for data leaks and nightmare headlines.
Privilege Escalation Issues
What’s Happening?
Privilege escalation is the classic “oops, wrong door” moment, except worse. Attackers play around with stuff like URL tweaks changing something like user_id=123 to user_id=456, just to slide into accounts that aren’t theirs. Honestly, I once fiddled with a QA app and, with a lucky guess, landed in some admin dashboard. Wildly irresponsible (and honestly, kind of hilarious).
Fix
- Server-Side Checks: Don’t trust the front end for anything serious. Always check permissions where the real power is i.e The server.
- Role-Based Access Control (RBAC): Map out who should do what. And actually stick to it.
- Deny by Default: Block access unless explicitly allowed.
- Log Access Attempts: Monitor suspicious activity to catch issues early.
Insecure Direct Object References (IDOR)
What’s Happening?
IDOR is when your app hands out IDs (like user_id, file_id) right in URLs or forms, letting people muck around and poke places they shouldn’t. Easy exploit, surprisingly common.
For example, changing a URL parameter to access another user’s file. I’ve seen this in apps where developers assumed users wouldn’t tamper with URLs.
Fix
- Indirect References: Use random, non-sequential identifiers or mapping tables.
- Access Checks: Verify the user has permission to access the specified resource.
- Obscure IDs: Avoid exposing database IDs in URLs or APIs.
- Rate Limiting: Limit how many requests a user can make to guess IDs.
Missing Function-Level Access Control
What’s Happening?
This happens when an app doesn’t check permissions for specific functions, like accessing an admin endpoint by directly navigating to it. I read about a case where a user accessed a hidden API endpoint just by guessing its path.
Fix
- Function-Level Checks: Validate permissions for every endpoint or function.
- Centralized Authorization: Use a single authorization layer to enforce rules.
- Hide Sensitive Endpoints: Don’t advertise your secret admin URLs like it’s a clearance sale.
- Penetration Testing: Regularly unleash the hackers (the good kind) on your stuff to see what breaks.
5. Security Misconfigurations
Security misconfigurations are the “forgot to lock the door” of web vulnerabilities. They’re so preventable, yet so common. These happen when systems aren’t properly hardened, leaving them open to attack. It’s like handing attackers a map to your weaknesses.
Unpatched Systems, Exposed Headers
What’s Happening?
Unpatched systems run outdated software with known exploits. Exposed headers, like server version info or debugging data, give attackers a starting point. I saw a breach once caused by an old WordPress plugin with a public exploit. It’s a painful lesson.
Fix
- Keep Software Updated: Patch servers, frameworks, and libraries regularly. Tools like Dependabot can help.
- Disable Unnecessary Features: Turn off directory listing or unused services.
- Hide Sensitive Info: Remove verbose error messages and headers like
X-Powered-By. - Use Security Scanners: Tools like OWASP ZAP can spot misconfigurations.
Default Configurations
What’s Happening?
Some apps are blessed with some default configurations like “admin123.” or “Admin@123” or “Administrator” etc. These kinds of username and passwords are heavily known to hackers and can be easily guessed, leaving the system vulnerable.
I’ve even seen servers that still have their original database login credentials, which is basically an open invitation for security breaches.
Fix
- Change Defaults: Always reset default usernames, passwords, and settings.
- Harden Configurations: Follow security best practices for your tech stack.
- Automated Checks: Use tools to scan for default or weak configurations.
- Documentation: Ensure your team knows to avoid default settings during setup.
Misconfigured Cloud Services
What’s Happening?
If you have not setup the “AWS S3 buckets” or “Azure blobs” properly then , They can also accidentally expose private information. It’s a common mistake with big consequences.
Fix
- Restrict Access: Set strict access controls on cloud resources.
- Enable Logging: Monitor access to cloud services for suspicious activity.
- Use IAM Policies: Enforce least privilege for cloud users and services.
- Regular Audits: Check cloud configurations with tools like AWS Trusted Advisor.
6. Insecure Deserialization
Insecure deserialization is a bit of a dark horse, it’s less common but can be catastrophic. It happens when an app turns untrusted data into objects without proper checks, potentially letting attackers run arbitrary code. It’s the type of thing you never think of about until it attacks you.
Remote Code Execution Risks
What’s Happening?
Attackers craft malicious payloads that, when deserialized, execute code on your server. I read about a Java app where this led to ransomware being installed. It’s terrifying how a small flaw can lead to total compromise.
Fix
- Avoid Untrusted Data: Don’t deserialize data from untrusted sources if possible.
- Whitelisting: Only allow specific classes or types during deserialization.
- Safe Formats: Use JSON or XML with strict parsing instead of complex objects.
- Monitor Behavior: Log and monitor deserialization for unusual activity.
Data Tampering
What’s Happening?
Hackers can mess with serialized data to change how an app acts, such as switching a user’s role from “guest” to “admin.” I came across a situation where a deserialized object allowed an attacker to gain higher privileges without being noticed.
Fix
- Integrity Checks: Use cryptographic signatures to verify serialized data.
- Strict Validation: Validate deserialized objects against expected structures.
- Avoid Complex Objects: Keep serialized data simple to reduce attack surfaces.
- Logging: Track deserialization attempts to spot tampering.
Denial of Service (DoS) via Deserialization
What’s Happening?
Attackers can craft serialized data to consume excessive resources, crashing your app. Think of it like sending a massive, complex object that overwhelms the deserialization process. I’ve heard of apps going down because of this kind of attack.
Fix
- Limit Resource Usage: Set limits on memory and CPU for deserialization.
- Validate Size: Check the size of serialized data before processing.
- Use Safe Libraries: Libraries like Jackson for Java can be configured securely.
- Rate Limiting: Limit how often users can send serialized data.
Reporting and Remediation: Turning Security Findings into Action
So, you’ve identified vulnerabilities in your web application, great! That’s half the battle. But now what ?
Finding the issues is one thing; reporting them clearly and fixing them properly is where the real work begins. I’ve been immersed in the world of web security recently, and it’s proving to be quite the challenge. The trick is to explain the issue at hand without coming across as a doomsayer, collaborate with developers who might already be stretched thin, and ensure that the solutions implemented are truly effective. It’s a learning experience, and I’ll freely admit that I’ve encountered some reports so unclear they only added to the bewilderment.
Let’s break down the crucial stages of reporting and addressing vulnerabilities, drawing on established best practices and insights I’ve gathered from my own journey.
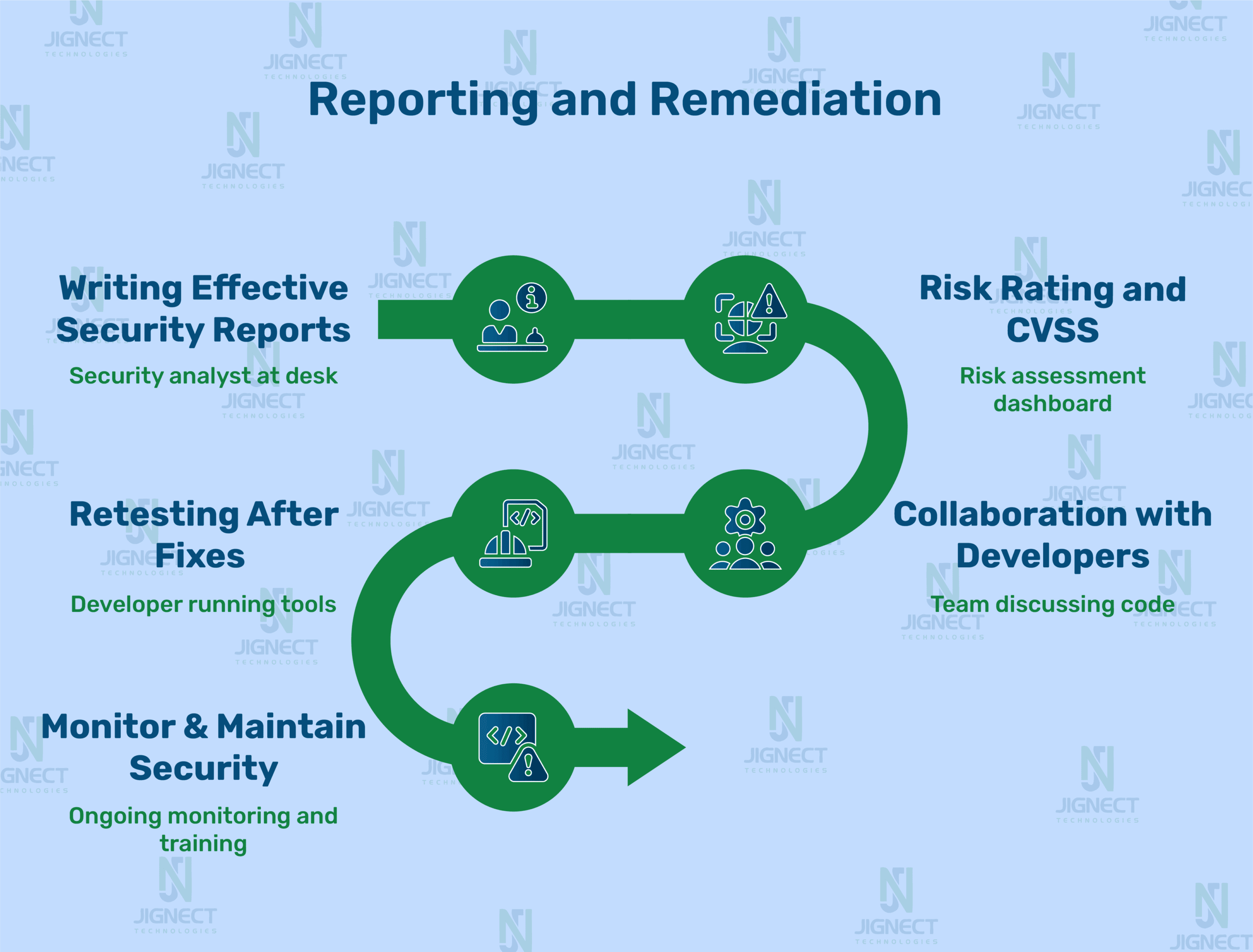
1. Writing Effective Security Reports
A great security report is like a great story which grabs you in and makes you think and does something with what you hear. I’ve come across reports that were just use of technical terms without purpose and also ones which any layman could understand. The difference? Structure and focus.
Structure, Clarity, and Impact
What’s the Issue?
A security report has to present the vulnerability in a simple and complex language at the same time. If it is too general developers will not know what to do; if it is too technical managers may ignore it. Structure it with a clear summary, detailed findings, and actionable steps.
I once saw a report that just said “XSS found” with no context, nobody knew where to start. Include specifics: where the issue is, how it was found, and why it matters.
How to Do It
- Use a Clear Format: Start with an executive summary, then dive into technical details (vulnerability type, location, impact). End with remediation steps.
- Be Concise: Avoid jargon overload. Say “malicious script in comment field” instead of “arbitrary code injection vector.”
- Show Impact: Explain the real-world consequences, like data theft or account takeover to get buy-in.
- Include Evidence: Screenshots, logs, or proof-of-concept code make the issue tangible.
Prioritizing Findings
What’s the Issue?
Not all vulnerabilities are the same. We see that presenting the issue as critical in all cases does not scale and also that which we minimize serious issues leaves us vulnerable. I have had it with teams that ignore reports which labeled everything as “urgent” which is a practice which does not help. Prioritizing findings helps focus efforts on what matters most.
How to Do It
- Use a Risk Framework: Reference frameworks like CVSS or your company’s risk matrix to rank issues.
- Highlight Critical Issues: Call out high-impact vulnerabilities (e.g., SQL injection) upfront.
- Group Related Findings: Bundle similar issues to avoid redundancy.
- Provide Context: Explain why a low-severity issue might still need attention in your app’s context.
Communicating to Stakeholders
What’s the Issue?
Level of detailing varies from audience to audience. Developers want technical specifics; executives want the big picture. I once put out a report which developers really got into but the management team had no interest in because it was too heavy on tech. The key to getting action is to tailor your report to your audience.
How to Do It
- Customize for the Audience: Use plain language for executives, technical details for developers.
- Visual Aids: Charts or diagrams can make complex issues easier to grasp.
- Actionable Recommendations: Suggest specific fixes, not just “patch this.”
- Follow Up: Offer to discuss the report with stakeholders to clarify questions.
2. Risk Rating and CVSS
Assigning risk ratings to vulnerabilities is a tool which helps teams to prioritize which to fix first, but that’s not to say it is a simple task of 1, 2, or 3. I have seen issues break out in which a flaw is debated to be of “high” or “medium” severity; we all have our own opinions.
Severity Metrics
What’s the Issue?
The present standard for vulnerability assessment is the Common Vulnerability Scoring System (CVSS) which we turn to for this purpose. It provides a 0 to 10 score which is determined by factors such as exploitability and impact. For instance a SQL injection which is easy to play out and which reports back large sets of sensitive data may receive a 9. But also it is important to note that CVSS is not without its flaws; it does not always take into account your application’s unique environment.
How to Do It
- Use CVSS as a Baseline: Calculate scores using the CVSS calculator (NIST’s site is handy).
- Adjust for Context: A “medium” CVSS score might be critical if it affects your core business logic.
- Document Assumptions: Explain why you rated a vulnerability a certain way.
- Combine with Other Metrics: Use internal risk frameworks alongside CVSS for accuracy.
Qualitative vs. Quantitative Ratings
What’s the Issue?
CVSS is quantitative, but sometimes a qualitative rating like “low, medium, high” resonates more with teams. I’ve found that developers sometimes glaze over numbers but perk up when you say “this could take down the site.” Balancing both approaches helps.
How to Do It
- Map CVSS to Qualitative: For example, CVSS 7–10 is “critical,” 4–6 is “medium.”
- Explain Impact: Tie ratings to business risks, like downtime or data leaks.
- Be Consistent: Use the same rating system across reports to avoid confusion.
- Involve Stakeholders: Get input from devs or managers to refine ratings.
Temporal and Environmental Factors
What’s the Issue?
CVSS includes temporal (e.g., exploit availability) and environmental (e.g., your app’s setup) factors that can change a score. For instance, a vulnerability with a public exploit is more urgent. I once underestimated a flaw because I didn’t know a proof-of-concept was already out there.
How to Do It
- Check Exploit Availability: Monitor sites like Exploit-DB for known exploits.
- Assess Your Environment: A vulnerability in a public-facing app is riskier than in an internal tool.
- Update Scores: Reassess ratings as new information (like patches) emerges.
- Document Changes: Note why a score changed in your report.
3. Collaboration with Developers
Fixing issues isn’t just about bringing up problems, it’s about working with developers to get solutions in place. I have had the security teams and developers at each other’s throats due to broken lines of communication which is a waste of energy.
Fixing and Validating Vulnerabilities
What’s the Issue?
Developers have a lot of different tasks at once, we aim to make their jobs easier, not harder.
Provide clear, actionable fixes and verify they work. I once suggested a fix that sounded great in theory but broke the app’s functionality.
How to Do It
- Provide Specific Fixes: Instead of “fix XSS,” say “use
htmlspecialcharsfor output.” - Offer Code Samples: Share snippets or references to secure libraries.
- Validate Fixes: Test the patch yourself to ensure it works without side effects.
- Be Available: Offer to pair with devs to troubleshoot tricky fixes.
Building a Security Culture
What’s the Issue?
If security is seen as a separate issue for others to deal with, you are at a disadvantage. Creating a culture of which all members care about security issues makes for easier remediation. I’ve seen teams transform when security became a shared goal.
How to Do It
- Educate, Don’t Lecture: Run workshops or lunch-and-learns on common vulnerabilities.
- Celebrate Wins: Acknowledge when devs fix issues well, it builds goodwill.
- Integrate Security Early: Push for secure coding practices in the design phase.
- Be Empathetic: Understand devs’ workloads and constraints.
Handling Resistance
What’s the Issue?
At times developers push back which may be due to skepticism or just being very busy. I have had developers bring up that a vulnerability is a small issue because it’s hard to exploit. Closing that gap takes tact and persistence.
How to Do It
- Explain the Why: Show how the vulnerability could hurt the business or users.
- Prioritize Fixes: Help devs focus on high-impact issues first.
- Compromise When Needed: If a full fix isn’t feasible, suggest temporary mitigations.
- Escalate Judiciously: Only involve managers if absolutely necessary.
4. Retesting After Fixes
Patching a vulnerability is not the end. Retesting to make sure the fix works and did not create new issues is required. I’ve seen “fixed” vulnerabilities resurface because nobody checked properly.
Ensuring Vulnerabilities Are Resolved
What’s the Issue?
A fix might look good on paper but fail in practice, maybe it only partially addresses the issue or breaks something else. I once tested a patch that stopped an XSS attack but caused a login form to crash. Retesting catches these gotchas.
How to Do It
- Replicate the Attack: Try the original exploit to confirm it’s blocked.
- Test Edge Cases: Check if the fix holds under different conditions (e.g., special characters).
- Use Automated Tools: Scanners like Burp Suite can help verify fixes.
- Document Results: Log what you tested and the outcome for accountability.
Regression Testing
What’s the Issue?
Fixes can break other parts of the app, especially in complex systems. Regression testing ensures the patch doesn’t mess up unrelated features. I’ve seen a security fix tank performance because it wasn’t tested thoroughly.
How to Do It
- Run Full Test Suites: Use automated tests to check core functionality.
- Focus on Impacted Areas: Test features related to the fix (e.g., forms for XSS patches).
- Monitor Performance: Ensure the fix doesn’t slow down the app.
- Involve QA: Work with the QA team to cover all bases.
Automated vs. Manual Retesting
What’s the Issue?
Automated tools can catch obvious issues, but manual testing often finds subtle flaws. I’ve had tools miss a DOM-based XSS because it required specific user actions. Balancing both is key.
How to Do It
- Use Scanners: Tools like OWASP ZAP can quickly verify common fixes.
- Manual Testing: Replicate complex attacks that tools might miss.
- Combine Approaches: Use automation for scale, manual for depth.
- Document Both: Note which tests were automated vs. manual for clarity.
5. Monitor & Maintain Security
Security is a continuous process, not a one time event. I have seen applications break into months after a “successful” audit that was reported out to the team. Monitoring and maintenance keep your app secure long-term.
Continuous Monitoring
What’s the Issue?
New issues present themselves constantly with new exploits, misconfigurations, or even human error. Which is why we have continuous monitoring which identifies issues before they turn into full scale disasters. I read about a company that got hit because they stopped monitoring after a big security push.
How to Do It
- Set Up Alerts: With Splunk or ELK, you can set up notifications when any suspicious activity appears in your logs.
- Vulnerability Scanning: Schedule Nessus or other similar tools, to scan your system on a regular basis.
- Monitor Dependencies: Track libraries for known vulnerabilities using tools like Dependabot.
- Incident Response Plan: Have a plan ready for when (not if) something goes wrong.
Patch Management
What’s the Issue?
Not patching your systems is a dream come true for hackers. Every day, there are updates and keeping track can be exhausting. Many teams have found that they regretted holding up patches due to their schedule.
How to Do It
- Prioritize Patches: Always keep eye on highly sensitive vulnerabilities like CVSS 7+.
- Automate Updates: Use tools to streamline patching where possible.
- Test Patches: Verify patches in a staging environment to avoid breaking production.
- Track Compliance: Ensure all systems meet your patch policy.
Security Awareness Training
What’s the Issue?
Humans are often the weakest link. Developers, admins, even users can introduce vulnerabilities if they’re not trained. I once saw a breach caused by a dev clicking a phishing link, training could’ve prevented that.
How to Do It
- Regular Training: Run sessions on secure coding, phishing, and best practices.
- Simulate Attacks: Use fake phishing emails to test awareness.
- Make It Engaging: Gamify training to keep it interesting.
- Update Content: Keep training current with new threats.
Best Practices: Incorporating Security into Your Web Applications
So you’ve identified vulnerabilities in your web application and reported them, now how do you make it secure in the long term?
That’s where best practices kick in. I’ve given this a lot of thought lately, particularly after observing how small tweaks early on can avert gigantic headaches later on.
Security doesn’t only mean patching things after a break-in has occurred; it means building applications that are hard to crack from the beginning. It’s akin to locking your doors when you depart the house, rather than rushing to do so after a robbery has taken place. In the modern era of web apps being the very targets for attacks on the digital frontier, from data theft through cross-site scripting (XSS), writing security into each development phase must be a necessity.
Let’s take a look at some key practices to secure your web applications better, combining industry standards and lessons learned along the way. Ideally, this will make security less overwhelming and achievable.
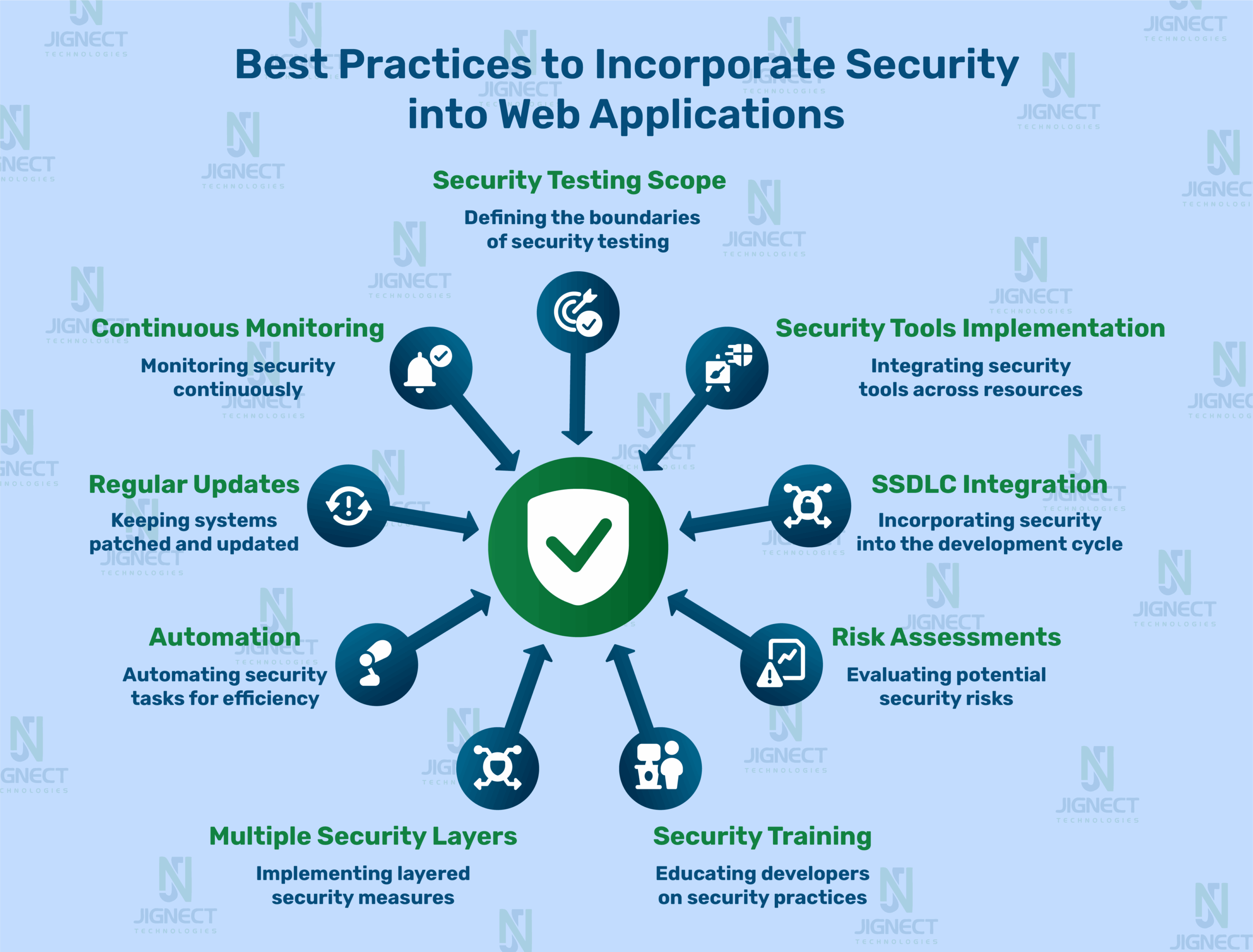
1. Adopt a Shift-Left Security Mindset
Shift-left security means finding issues early on, long before your application goes live. I used to think of security as something you added on at the very last minute, like plugging a leak in a boat after it’s already on the water.
It’s so much better when you solve security in design and code, less time wasted, less stress and mayhem. The majority of vulnerabilities creep in through development because security isn’t taken into account right at the beginning.
I used to watch a team frantically patch an XSS vulnerability on the eve of a product launch, absolute mayhem. By building security early on, you identify issues when it’s less costly and less time-consuming to solve them.
- Plan Security Early: Involve security experts at the design phase of the project. Do threat modeling (see below) and establish countermeasures for security risks like data leakage or unauthorized access beforehand.
- Employ Secure Frameworks: Select a framework like Django or Spring containing default protections against popular attacks like CSRF or SQL injection.
- Train Developers: Educate your staff on secure coding fundamentals, such as input validation, from resources such as OWASP’s Top Ten or secure coding standards.
- Test Early: Make use of tools like SonarQube to find issues at the time of development only to stop them from going into production.
- Secure Development Lifecycle (SDLC): Integrating security into each stage, from gathering requirements to designing, developing, testing, and deploying is crucial. Utilizing frameworks such as OWASP SAMM is not only a wise move but also simplifies the process and ensures comprehensive security coverage.
Actionable Tip: When evaluating outside libraries, include solutions like OWASP Dependency-Check in your planning workflow, so you spot vulnerabilities before anything is integrated into your product. It’ll save headaches for both engineering and security down the line.
2. Adhere to Secure Coding Practices
Secure programming isn’t simply being cautious, it’s about obeying established proven rules. I’ve written bad code before and learned the hard way that a little bit of discipline can make a big difference. Secure programming is like a seatbelt: easy but life-saving. Poorly written code may open doors for attackers. Not validating user inputs, for example, may result in SQL injection or XSS attacks. I came across a site that got compromised because they didn’t escape their user input properly, so small a slip-up, so huge a disaster.
- Validate All Inputs: Always check what users provide, forms, URLs, everything, against allowlists. Block anything that looks suspicious. For example, make sure an email input only accepts properly formatted email addresses.
- Sanitize Inputs: Escape or remove malicious characters before doing anything with them. Use libraries like DOMPurify to clean up HTML and avoid XSS.
- Escape Outputs: Convert special characters (like < or >) into safe versions before showing them to users to prevent XSS.
- Use Safe APIs: Stick with secure functions like prepared statements when working with databases to dodge SQL injection.
- Limit Error Messages: Don’t reveal too much in error outputs, no stack traces or DB errors that attackers could use.
Example (Node.js with Express):
const express = require('express');
const app = express();
const validator = require('validator');
// Validate and sanitize input
app.post('/user', (req, res) => {
const username = validator.escape(req.body.username); // Sanitize input
if (!validator.isAlphanumeric(username)) {
return res.status(400).send('Invalid username');
}
// Proceed with safe input
});Actionable Tip: Use libraries like validator.js in Node.js or filter_var() in PHP to make input validation and sanitization easier and more reliable.
3. Enact Strong Authentication and Authorization
Weak authentication and loose access control are open doors for attackers. I’ve seen apps get breached due to basic mistakes, like weak passwords or giving users more access than they need. You need solid checks to verify who’s who and tightly control what they can do.
- Multi-Factor Authentication (MFA): Days of depending solely on passwords are over. Ask users to prove who they are not just with a password, but also with a unique code that gets sent to their phone. It’s an easy extra step that boosts your security big time.
- Secure Password Storage: Keep user credentials safe by using tried-and-true techniques. Hash passwords with strong methods like bcrypt, Argon2, or PBKDF2. Weak or old-fashioned hashing just makes your business a sitting duck.
- Role-Based Access Control (RBAC): Set up roles with specific permissions and stick to the principle of least privilege. Don’t give users more access than necessary.
- Session Management: Protect session cookies by marking them as HttpOnly, Secure, and setting a SameSite attribute. Also, use short timeouts and invalidate sessions on logout.
Example (Secure Cookie in Express):
app.use(session({
secret: 'your-secret-key',
cookie: {
secure: true,
httpOnly: true,
sameSite: 'strict'
},
resave: false,
saveUninitialized: false
}));Actionable Tip: For user authentication, stick with industry-standard protocols like OAuth 2.0 or OpenID Connect. Avoid building your own authentication system unless you want to invite security headaches down the line.
4. Secure APIs and Third-Party Integrations
APIs are super useful, but without proper protection, they can spill your company’s secrets.
A single unsecured API endpoint can let sensitive data slip out in mere seconds. Always see your integrations as top-priority and protect them accordingly.
- Implement HTTPS: Always enforce HTTPS to encrypt data during transmission. Redirect any HTTP traffic to HTTPS automatically.
- Verify API Requests: Use API keys, OAuth tokens, or JWTs, and make sure to validate them every single time.
- Rate Limiting: Set limits to prevent abuse and defend against DoS attacks.
- Audit Third-Party Integrations: Regularly check all libraries and external services with tools like Snyk or OWASP Dependency-Check.
Actionable Tip: Use API gateways (like AWS API Gateway or Kong) to manage things like authentication and rate limits in one place.
5. Perform Periodic Audits and Updates
Ongoing Audits & Updates Think of application security like regular maintenance on business infrastructure. Staying proactive with updates prevents minor issues from turning into serious breaches. It’s surprisingly common for attackers to exploit simply outdated libraries.
- Schedule Audits: Run security scans every few months, tools like OWASP ZAP or Nessus are effective and reputable for finding vulnerabilities.
- Update Software: Patch your frameworks, libraries, and servers regularly. Dependabot can help automate this.
- Verify Configurations: Disable default credentials, close unused ports, and harden all settings.
- Log and Review: Monitor logs for anything unusual and go through them regularly to catch early signs of trouble.
Actionable Tip: Use a vulnerability management process that prioritizes updates based on severity (like using CVSS scores).
6. Conduct Threat Modeling
Threat modeling can totally change the game. It’s about thinking like a hacker and spotting weak points before they become problems. I’ve skipped this step before and ended up regretting it, we had to fix avoidable issues post-launch.
- Map Your Application: Lay out all the pieces, APIs, databases, user inputs, and how they interact.
- Find Threats: Think about what could go wrong (like unauthorized access) using a framework like STRIDE.
- Prioritize Risks: Focus on what’s likely to happen or could cause the most damage.
- Plan Defenses: Add the right protections, like encryption or access controls, based on what you discover.
Actionable Tip: Use something like Microsoft’s Threat Modeling Tool to make this easier and more structured.
7. Defend Against Common Vulnerabilities
The OWASP Top Ten is your cheat sheet for web security risks, and there are proven fixes for each.
- Cross-Site Scripting (XSS): Set strict CSP headers and always escape output based on context.
- Cross-Site Request Forgery (CSRF): Protect forms with CSRF tokens and validate them on the server.
- Insecure Deserialization: Never deserialize data you don’t trust. Stick to safer formats like JSON.
- Security Misconfigurations: Lock down your servers, disable directory listings, delete unused accounts, and keep software updated.
Example (CSP Header in Express):
app.use((req, res, next) => {
res.setHeader("Content-Security-Policy", "script-src 'self' 'trusted-cdn.com'");
next();
});Actionable Tip: Keep doing regular testing with tools such as OWASP ZAP or Burp Suite. It’s better to identify weaknesses internally before they’re exploited from the outside.
8. Encrypt Data at Rest and in Transit
Data protection isn’t just best practice, it’s required for compliance and building trust with your users.
- Encrypt in Transit: Use TLS 1.3 with strong ciphers. Disable old protocols like SSL.
- Encrypt at Rest: Secure all stored business data with strong encryption, such as AES-256.
- Key Management: Handle encryption keys responsibly. Leverage enterprise solutions like AWS KMS or HashiCorp Vault to keep your keys protected and your business compliant.
Actionable Tip: Let’s Encrypt offers free SSL/TLS certificates, no excuse not to use encryption.
9. Test and Monitor Periodically
Don’t wait for a security incident to find out something’s broken. Ongoing testing and monitoring are your first lines of defense.
- Static Analysis (SAST): Use tools like SonarQube to catch issues while coding.
- Dynamic Testing (DAST): Run OWASP ZAP on your live apps to see how they behave under attack.
- Penetration Testing: Simulate real attacks to expose hidden vulnerabilities.
- Logging and Monitoring: Track what’s happening in real time with tools like the ELK Stack or Splunk.
Actionable Tip: Hook security scans into your CI/CD pipelines using GitHub Actions or Dependabot.
Security Testing Standards & Guidelines: A Simple Guide to Keeping Your App Safe
To more easily relate to the idea of testing your web app for security, think of it like checking your house for vulnerabilities before a storm (being sure to close the windows). I’ve and have been looking into security standards lately and, honestly, it’s a lot, but it’s worth it! Standards are there to help you identify issues and vulnerabilities before a hacker does. The OWASP Top 10 is the big one and I am going to take a look at it in some detail, using their official descriptions and information found on OWASP’s site since it’s so prevalent. There are other security standards, like NIST and PCI-DSS, and I am going to go through these standards, too, with their basic descriptions and some practical suggestions. I hope this makes security testing feel a bit more like a plan and less like a task.
1. OWASP Top 10
The OWASP Top 10 is essentially a “most wanted” list of the most critical security vulnerabilities found in web applications.
It serves as a crucial reference for developers and security professionals alike, and I recall my initial reaction to it being, “Wow, there are a ton of things that could potentially go wrong!” This list is widely acknowledged as the starting point for creating more secure code, and businesses rely on it to foster a culture of secure development practices.
Just a heads-up: OWASP is currently working on the 2025 edition of the Top 10, which is expected to be released in the first half of 2025. They’re gathering application testing data until December 2024, so if you have any relevant statistics to contribute, head over to owasp.org.
For now, let’s explore the 2021 version, which is the most current one available.
Frequent Vulnerabilities and Resolutions
What’s the Problem?
- The OWASP Top 10 for 2021 lists the most critical risks with some omissions and updates from past editions. Here is the summary based on OWASP’s official list:
- A01: Broken Access Control: Moved up from #5, this is super common, 94% of apps tested had issues here. It’s when users can access stuff they shouldn’t, like viewing another user’s data by tweaking a URL.
- A02: Cryptographic Failures: Up from #3, this used to be called Sensitive Data Exposure. It’s about weak encryption letting attackers steal data, like passwords.
- A03: Injection: Down to #3, this includes SQL injection and XSS (now part of this category). 94% of apps were tested for injection, and it’s still a big threat. I once saw a login form hacked with a simple SQL trick.
- A04: Insecure Design: New for 2021, this is about flaws in how the app is built, like not planning for security early.
- A05: Security Misconfiguration: Up from #6, this covers things like unpatched software or exposed settings. It now includes XML External Entities (XXE).
- A06: Vulnerable and Outdated Components: Up from #9, this is about using older libraries that we know have problems. This is hard because it doesn’t match CVEs but is a huge risk.
- A07: Identification and Authentication Failures: Down from #2, this covers weak passwords or session issues. Standardized frameworks are helping here.
- A08: Software and Data Integrity Failures: New for 2021, this includes issues like unverified software updates or insecure deserialization (from 2017’s list).
- A09: Security Logging and Monitoring Failures: Up from #10, this is about not catching attacks because of poor logging. It’s hard to test but critical.
- A10: Server-Side Request Forgery (SSRF): New from the community survey, this is when attackers trick your server into making harmful requests. It’s less common but has high impact potential.
How to Do It
- Broken Access Control: Check permissions on the server, not just the UI. Use role-based access control (RBAC).
- Cryptographic Failures: Use strong encryption (like TLS 1.3) and secure key storage. Avoid outdated algorithms like MD5.
- Injection: Validate all inputs and use prepared statements for databases. Escape outputs to block XSS.
- Insecure Design: Use threat modeling and secure design patterns from the start. I learned this the hard way when a rushed project led to flaws.
- Security Misconfiguration: Keep software updated and hide sensitive info, like server versions, in error messages.
- Vulnerable Components: Use tools like OWASP Dependency-Check to identify where old libraries are present.
- Authentication Failures: Implement strong passwords and multifactor authentication (MFA).
- Integrity Failures: Verify software updates and use secure CI/CD pipelines.
- Logging Failures: Set up logs to catch suspicious activity and test them regularly.
- SSRF: Validate and restrict server requests to trusted URLs only.
Prioritizing OWASP Risks
What’s the Issue?
With 10 risks, it’s easy to get overwhelmed. Not every issue is critical for your app, say, SSRF might be less urgent if your app doesn’t make many server requests. I’ve seen teams waste time on low-risk issues while ignoring stuff like broken access control, which is a huge deal since it’s #1 for a reason.
How to Do It
- Know Your App: Figure out which risks (like injection or misconfiguration) are most likely for you.
- Use CVSS Scores: Combine OWASP with CVSS to rank severity. For example, broken access control often scores high.
- Focus on Top Risks: Start with A01-A03 (access control, crypto, injection) since they’re common and dangerous.
- Track Progress: Document which risks you’ve addressed and why.
Training Teams on OWASP
What’s the Issue?
The OWASP Top 10 is only useful if your team gets it. I once worked with developers who thought security was “someone else’s job,” and it led to messy fixes. Training everyone starting from coders, testers, even managers makes security a team effort.
How to Do It
- Run Workshops: Teach the Top 10 in simple terms, using examples like SQL injection.
- Add to Code Reviews: Check for OWASP issues when reviewing code.
- Use Free Resources: OWASP’s site has cheat sheets and guides, It’s super helpful.
- Encourage Questions: Let your team ask about risks without feeling dumb.
2. NIST Guidelines
NIST guidelines are in a way a very thorough checklist for testing security. Not the best read, but will help ensure that you’ve considered everything.
Testing Procedures and Controls
What’s the Issue?
NIST (like SP 800-53) gives you steps to test things like access controls, encryption, and logging. Without a plan, you might miss big flaws. I saw a team once skip encryption tests and regret it when sensitive data got exposed.
How to Do It
- Follow NIST Steps: Test key areas like user authentication and data protection.
- Schedule Tests: Run checks regularly, not just once a year.
- Keep Records: Write down what you tested and what you found.
- Use NIST Tools: The NIST Cybersecurity Framework is a great starting point.
Risk Assessment Processes
What’s the Issue?
NIST pushes you to think about what could go wrong, like weak passwords letting attackers in. Skipping this can leave you blind to risks. I’ve seen apps get hit because nobody assessed the risks of an exposed API.
How to Do It
- List Threats: Identify risks like data theft or unauthorized access.
- Measure Impact: Decide how bad each risk would be for your app.
- Add Protections: Use things like encryption or access limits to reduce risks.
- Check Often: Update your risk list as your app grows.
Incident Response Planning
What’s the Issue?
NIST says you need a plan for when things go wrong, like a hacker getting in. Without one, you’re lost in a crisis. I read about a company that lost hours because they didn’t know how to respond to a breach.
How to Do It
- Make a Plan: Outline how to spot, handle, and recover from attacks.
- Practice It: Run drills to test your plan with your team.
- Assign Jobs: Decide who does what during a security issue.
- Keep It Fresh: Update your plan as new threats pop up.
3. CWE/SANS Top 25
The CWE/SANS Top 25 is with regard to finding the coding mistakes that can lead to a large security risk. (i.e., warning list). It is a list for developers to point out errors that they commonly make.
Most Dangerous Software Errors
What’s the Issue?
This list covers errors like buffer overflows or weak input validation that let attackers take over your app. I once saw a small coding mistake cause a crash because of a buffer overflow, it was a mess.
How to Do It
- Check Inputs: Always validate what users send to avoid errors like overflows.
- Use Safe Code: Avoid risky functions, like
strcpyin C, that can cause problems. - Secure Logins: Use strong password hashing, like bcrypt, to avoid auth errors.
- Review Code: Look for Top 25 errors before launching your app.
Static Analysis for CWE
What’s the Issue?
Tools can catch CWE errors, like bad error handling, before they become problems. I’ve seen teams miss these because they only did manual checks, which take ages.
How to Do It
- Use Tools: Run static analysis with tools like Fortify to find errors.
- Scan Early: Check code during development, not just at the end.
- Fix Big Issues First: Focus on errors that could cause major vulnerabilities.
- Train Coders: Teach your team how to spot and fix CWE issues.
Error Handling Best Practices
What’s the Issue?
Bad error handling, like showing detailed error messages, can give attackers hints about your system. I saw a site once leak database info in an error. It’s a big mistake.
How to Do It
- Hide Details: Show users simple error messages, not techy ones.
- Log Safely: Save detailed logs for your team, but keep them secure.
- Test Errors: Make sure your app handles errors without crashing.
- Use Frameworks: Tools like Django have safe error handling built in.
4. PCI-DSS for Web Security
PCI-DSS is a strict set of rules for apps that handle credit card info. If you’re running an online store, this is non-negotiable. I’ve heard of businesses getting huge fines for ignoring it.
Security Checklist for Payment Apps
What’s the Issue?
PCI-DSS requires things like encrypting card data and securing your network. If you slip up, you risk data theft or penalties. I read about a store that got fined millions for a weak password.
How to Do It
- Encrypt Card Data: Use strong encryption (like TLS) for card info at all times.
- Secure Your Network: Set up firewalls and limit who can access payment systems.
- Test Often: Run scans and penetration tests to meet PCI rules.
- Limit Access: Only let trusted staff touch cardholder data.
Vulnerability Management
What’s the Issue?
PCI-DSS says you need to find and fix vulnerabilities fast. An unpatched system could let attackers steal card info. I’ve seen companies struggle because they didn’t have a clear fix process.
How to Do It
- Scan Regularly: Use tools like Nessus to find weak spots.
- Fix Quickly: Patch critical issues within 30 days, per PCI rules.
- Track Fixes: Keep a log of what you fixed and when.
- Automate Scans: Use tools to make scanning easier.
Third-Party Vendor Security
What’s the Issue?
If you use third-party services, like payment gateways, they must follow PCI-DSS too. A weak vendor can be a weak link. I saw a breach once caused by a vendor’s bad security.
How to Do It
- Check Vendors: Make sure vendors are PCI-compliant.
- Monitor Them: Regularly review their security practices.
- Share Less Data: Only give vendors the data they need.
- Use Contracts: Add security rules to vendor agreements.
5. ISO 27001 for Security Management
I’m adding ISO 27001 because it’s like a big-picture guide for managing security across your whole organization, not just your app. It ties everything together nicely.
What’s the Issue?
Without a clear security plan, your efforts can be all over the place. ISO 27001 helps you organize your security processes. I’ve seen teams get lost without a framework like this.
How to Do It
- Build a Security Program: Set up policies for risks, incidents, and more.
- Train Your Team: Make sure everyone knows security basics.
- Audit Regularly: Check if your processes meet ISO 27001 standards.
- Keep Improving: Use audit results to make your security better.
Conclusion
Web application security testing isn’t just a technical checkbox, it’s a mindset, a habit, and, frankly, a necessity in today’s digital world. As we’ve seen, even a single overlooked vulnerability can lead to massive breaches, financial losses, and irreparable damage to reputation. The landscape is always shifting; new threats emerge, old ones evolve, and attackers keep finding creative ways to exploit the smallest cracks.
What stands out is that security testing is not a one-off event. It’s an ongoing process that should be woven into every stage of development and maintenance. Whether it’s internal security teams, QA engineers with a security focus, ethical hackers, third-party specialists, or the global community of bug bounty hunters, each brings a unique perspective that strengthens the whole.
Ultimately, the goal is not just to pass a test or tick a compliance box, but to build resilient, trustworthy web applications that protect users and businesses alike. The cost of ignoring security is simply too high, and the benefits of a proactive, layered approach are clear. By making security testing a routine part of your workflow, and by staying curious, vigilant, and open to new threats, you can help ensure that your web applications remain safe, reliable, and ready for whatever comes next.
We hope this guide gave you real clarity on how to secure your web applications with confidence. But we’re just getting started.
Up next, we’ll shift gears and dive into something just as critical – “Mobile App Security Testing: A Practical Guide for Modern QA Teams.” From code tampering to insecure storage and platform-specific threats, mobile apps bring a whole new set of challenges.
Get ready to explore how to secure your apps where users tap, swipe, and trust you the most. Stay tuned- it’s going to be a deep dive worth taking.
Witness how our meticulous approach and cutting-edge solutions elevated quality and performance to new heights. Begin your journey into the world of software testing excellence. To know more refer to Tools & Technologies & QA Services.
If you would like to learn more about the awesome services we provide, be sure to reach out.
Happy Testing 🙂




