Think of your smartphone as a vault, keeping your secrets, finances, and your digital life, all within the confines of the app. A simple vulnerability within the app can allow hackers to dance right into your life. Mobile apps are being attacked with threats that are as frequent as the taps, taps, swipes, and updates, making the security of mobile apps a game of high stakes that you cannot lose. The difficulty is that threats develop at an average speed much faster than you can say “app update,” not to mention the complexity of a mobile ecosystem that rarely makes security easy. Speed to deploy features often times means that security can take a backseat, and users want the app to work without concerns of privacy or security.
In this blog, we’ll take a practical look at why mobile application security testing matters more than ever, walking you through every phase, from identifying attack vectors like insecure storage, communication flaws, and code tampering. We will address the types of the most common attacks, who should be testing, and the critical steps to making security a critical pillar of trust and adoption in your app. There is no question, if you are building, testing or managing mobile apps, you have a role in understanding these threats and testing for them. Hopefully you will be able to recognize, and test for, problems specific to mobile, be aware of platform specific issues like rooting or jail breaking, understand how to turn on hardware-backed security, and are aware of best practice in reporting and remediation.
Once you finish this guide, you will be in a much better position to protect users data, understand and follow industry best practices, and have security checkpoints at every step in your development life cycle turning mobile security from an afterthought into a feature. Let’s get started!
- Introduction to Mobile App Security
- Why Mobile Application Security Testing Matters ?
- Common Mobile Attack Types
- Who Conducts Mobile Application Security Testing?
- How Mobile App Security Testing Is Performed?
- Security Testing Types for Mobile App
- Manual Testing
- Automated Testing
- Mobile Security Scanners (MobSF, Drozer aka your digital bloodhounds)
- Static Application Security Testing (SAST) for Mobile
- Dynamic Application Security Testing (DAST) for Mobile
- Interactive Application Security Testing (IAST) for Mobile
- Software Composition Analysis (SCA) for Mobile Dependencies
- Secret Scanning in Mobile Apps
- Fuzz Testing for Mobile Apps
- Testing Approaches
- Common Mobile Application Vulnerabilities
- Mobile Device and Platform-Specific Security Considerations
- Reporting and Remediation: Turning Mobile Security Findings into Action
- Best Practices: Incorporating Security into Your Mobile Applications
- Implement Shift-Left Security in Mobile
- Use Safe Coding Methods for Mobile
- Use Strong Login Security and Access Controls
- Keep Mobile APIs and Third-Party Connections Secure
- Run Mobile Audits and Keep Everything Updated
- Take Steps to Model Mobile Threats
- Reduce Common Mobile Security Risks
- Encrypt Mobile Data at Rest and in Transit
- Test and Monitor Mobile Apps Periodically
- Mobile Security Testing Standards & Guidelines
- Conclusion
Introduction to Mobile App Security
Smartphones are not just a tool for communication in this hyperconnected world: they are personal safes, business workstations and entry points to sensitive data. This centrality has led smartphones to the center of a global security breach. Attackers no longer settle on desktop attacks, they run sophisticated espionage campaigns and even sophisticated malware directed fully against mobile apps. Mobile attacks take advantage of mobile app unique vulnerabilities like poorly protected API’s or improperly configured cloud integrations, which are often undetected until a breach occurs.
The financial and reputational damage associated with breaches is highly inaccurate. Data shows that the average cost of a data breach is now $4.8 million, and mobile incidents are a big part of that increase. In an investigation, the scope of damage does not include the loss of data, decreased productivity, and the loss of user trust in the app. Often, it can take years for a company to repair damage to brand reputation and trust with customers.
If the threat landscape isn’t daunting enough, it is evolving at a rapid pace, and with great complexity. Attackers can be very agile, taking advantage of not just malware, but more obscure ways of attacking such as multi-factor authentication (MFA) fatigue or social engineering. Users are often the weakest chain in the mobile security chain despite being the target audience. Users fall victim to phishing, access unsafe networks, or some never consider upgrading their software.
On one hand, developers have to release features faster, which may not allow for thorough security measures. Conversely, developers contend with more hidden, structural attack surfaces from APIs and cloud services that may be out of view for those securing and monitoring access and system and application interfaces. In either event, security should be engraved, rather than bolted on. Security should be part of all mobile app development efforts, from inception through implementation. Security will become a primary component related to user acceptance and adoption. Security should also exceed beyond protection of sensitive data. It should also allow organizations to effectively address regulatory requirements and build user trust in their mobile entity.
Why Mobile Application Security Testing Matters ?
Mobile application security testing is no longer a “nice to have,” it is a critical requirement if an organization wants to protect their users, their reputation, and their business continuity. Most apps handle personal and financial data, and many apps handle sensitive data. There is a lot at stake.
We have listed some strong reasons for why security testing every mobile app is truly essential:
- Securing User Data & Privacy Security testing protects sensitive user data – personal data, payment data or credentials – from unauthorized access and leaks. Finding vulnerabilities early allows organizations to limit leaks of sensitive data which could harm users and destroy trust in an organization.
- No Damage to Reputation & Money Lost An incident can be extremely costly. Companies can incur financial losses in the millions, legal liabilities or even damage their brand for a long time. Proper security testing can only mitigate the risk of such breaches, and create confidence in your customer base.
- Compliance with Regulations & App Store Guidelines Regulating data under frameworks like GDPR, HIPAA or PCI DSS, or undergoing enforcement measures within app stores like Apple or Google Play, by having security testing you can limit the risk of hefty fines, app removal, app rejection and generally ensure your app is in good standing.
- Lowering Future Maintenance Costs Finding and remediating vulnerabilities early in the build of your software is much cheaper if they are identified before release, just like finding and fixing a leak in a boat before it sinks. Finding exploitable vulnerabilities in your software as early as possible is beneficial because it extends the vulnerability fix solution lifespan, eliminates the need for costly expensive emergency fixes, and lowers technical debt. Even if it seems costly now, investing in testing will lead to significant gains in avoiding maintenance costs down the road.
- Making Secure Releasing an Easy Ride Within DevOps Pipelines By embedding security testing into your CI/CD pipelines, you are evaluating weaknesses each time you have a release. The more times you can evaluate a security error the faster, easier and consistently you can safely deploy. This is immensely critical for helping you keep up with the pace of developing modern applications today.
- Creating User Trust and Brand Loyalty Users will ditch an app that they don’t trust, and one security incident can deeply harm your reputation. Regularly assessing your software for security issues signals to your users that you are valuing their safety and security as a user, which additionally creates loyalty and puts your app in place as a reliable candidate with positive engagement and overall brand integrity in a noisy market. Users generally engaging with and sharing apps that they deem safe and reliable.
- Discovering a Risk Early by Continuous Testing Waiting until you’ve been attacked to uncover exploitable vulnerability is a bet you cannot afford! Continuously testing security throughout the app lifecycle will enable your organization to discover vulnerabilities you would otherwise not be able to, and then be exposed by an attacker. This approach helps safeguard your users, and more importantly, consistently testing throughout the development phase can actually speed up your progress. By uncovering vulnerabilities earlier, it cuts down on the time needed for rework.
Okay, absolutely. Making sure your mobile apps are secure is the very first thing you need to do to protect user information, meet all the necessary rules and regulations, and make sure your app actually succeeds. By building security measures right into how you create and release your app, you’re not just protecting your business, you’re also building trust and creating strong connections with the people who use it.
Common Mobile Attack Types
Mobile applications pose a sometimes appetizing target for cybercriminals, as they often contain sensitive information (from personal information to financial credentials). Attackers exploit vulnerabilities found only in mobile environments which include a host of inter-related factors including mobility and connectivity, and a growing number of software ecosystems in play. Developers and security teams must know about common attack types to build applications which will keep users’ information safe from threats like those that can lead to data breaches, financial impacts, and loss of trust for existing users.
This article identifies and explains the most common mobile attack types, how they operate, and gives examples of real-world mobile attacks.
Insecure Data Storage
How It Works
Insecure data storage occurs when sensitive data, such as user id/password, payment data, or PII remains available on a mobile device, with no adequate encryption or protection. Insecure data storage is an attack vector for attackers when they have access to the device physically, using malware or accessing 3rd-party apps that are vulnerable. An attacker gains access to unprotected data without encryption or protection, such as databases, plaintext files, or sandbox areas of an app. A serious concern of insecure data storage is when devices are shared or stolen, as these attackers have minimal obstacles to retrieve data from insecure data storage.
Real-World Example
Back in 2018, a widely-used fitness app was found to be storing GPS coordinates and workout data in unencrypted files on Android phones. If someone had access to a rooted device, they could have easily grabbed this unprotected information, allowing them to track both the user’s location and their exercise routines. The incident sparked concerns about user privacy that led the app to strongly encrypt local storage data thereafter. Read more
Insecure Communication
How It Works
Insecure communication happens when an application transmits sensitive data (login credentials or financial information) over unencrypted or weakly encrypted channels. An attacker can capture this data by performing a man-in-the-middle (MITM) on an unsecured channel, one of the most common sources of weak security because of easy to attack unsecured Wi-Fi networks. Attackers took advantage of the absence or outdated TLS/ SSL protocols to capture user data that’s vulnerable to eavesdropping.
Real-World Example 1. Back in 2017, a few big banks like HSBC and Santander ran into trouble with the way they configured the security on their mobile apps. These SSL/TLS mistakes created a vulnerability known as a MITM attack. Essentially, this meant that anyone on the same public Wi-Fi network could have potentially stolen login information. This compromised thousands of accounts, prompting urgent updates to enforce proper encryption. Read More
Reverse Engineering and Code Tampering
How It Works
Reverse engineering is basically taking an app’s code apart, like unzipping it, to figure out exactly how it functions. Code tampering, on the other hand, involves actually modifying the app itself, usually with the goal of getting around security measures, unlocking premium features for free, or even sneaking in malicious software. Decompilation tools such as decompilers are known for weaknesses in code obfuscation, exploiting the functionality of Android and its open ecosystem that doesn’t have any too restrictive. Both of these techniques have devastating revenue impacts for app developers in addition to opening the door for data theft, unauthorized access, or distributing malicious versions of an app.
Real-World Example
In 2016, Pokémon GO, a sensitive location-based mobile game, was reverse engineered and enabled hackers to modify or tamper versions of the app that defeated local location-based play restrictions and enabled free in-app purchases. These modified applications were served on third-party app stores that generated new revenue loss for the game and exposed unsuspecting user devices to malware. Developers of the game responded to the level of code without escalation to 9 days of improved code obfuscation strategies and integrity checks going forward. Read more
Insecure Authentication
How It Works
Insecure authentication manifests when an application fails to sufficiently validate user identities from various weaknesses such as weak session management, predictable session tokens, or insecure biometrics. Attackers exploit insecure authentication to bypass the login altogether and take advantage of a compromised user account, or access sensitive features of the application. This is more serious if the application exposes the user to financial or personal data.
Real-World Example
In 2019, a popular ride-sharing application had insecure session token management in that it could predictively expose session IDs. An attacker was able to hijack user accounts and start unauthorized rides (along with other account abuse). As a result, the company completely overhauled its authentication system by implementing strong token randomization and defining short session expires. Read More
Side-Channel Attacks
How It Works
Side-channel attacks exploit unintended information leakages due to the physical, or operational, characteristics of devices, such as power consumption, touch-screen occurrences, or sensor data (gyroscope, accelerometer, etc.). Attackers are able to exploit these sources of information leakage to infer sensitive information (passwords, cryptographic keys, etc.) without even looking at the app code. Mobile devices are particularly prone to side-channel attacks provided they are full of sensors and many opportunities to leak information via sensor data.
Real-World Example
In a 2017 paper, an attacker used accelerometer data as a side-channel attack against a mobile payment app, reconstructing the known PIN values using location data from the touchscreen of the mobile device. The attack itself used subtle movements of the device to reconstruct user input. There are significant implications for the research, and apps must be do a better job assessing whether information from sensors is being used or not and if there is any protections against these unconventional types of attacks. Read More
Who Conducts Mobile Application Security Testing?
Mobile application security is a battlefield, and the armies that therefore defend your app are diverse. Within the ranks of these armies, the personnel are a variety of skills that can outwit the clever sleuths or cybercriminals they are battling. From house guards (those working for the App) to world hacker collectives, these positions are the leading roles in a strong defense against the threats that could destroy your App. Here is each of the critical players in battle to make sure that your mobile app can withstand any attempt to attack. Each will have their own operating advantage (which is unconventional) to help fend off cybercriminals.
- Internal Mobile Application Security Teams
- QA Engineers with Mobile Application Security Experience
- Ethical Hackers and Mobile Application Penetration Testers
- Third-Party Mobile Application Security Companies
- Bug Bounty Programs for Mobile Applications
- Automated Security Tools Managed by DevSecOps Teams
Internal Mobile Security Teams
What Makes Them Unique:
- They have a really deep understanding of how the app is built and what business goals it supports.
- They work smoothly alongside development teams to fix security issues as they arise.
- They create custom threat models designed specifically for the organization’s mobile environment.
- They are committed to fostering a security-first mindset throughout the entire company over the long term.
These internal tech heroes are the foundation of your app’s security, completely immersed in your organization’s mobile world. With a deep grasp of your app’s code, underlying systems, and business goals, they create custom security plans that really work. Whether they’re reviewing code or building threat models to predict your app’s specific dangers, they make sure security is built into every part. Think of them as the designers of a digital stronghold, collaborating closely with developers to close up any weak spots before anyone can take advantage of them, making sure your app is as tough as it is cutting-edge.
QA Engineers with Mobile Security Expertise
What Sets Them Apart:
- They combine their skills in quality assurance with a deep understanding of security, allowing them to perform comprehensive testing.
- They concentrate on spotting potential weaknesses early on, right within the development process.
- They are adept at using mobile-specific tools, such as MobSF, to conduct focused security assessments.
- They act as a crucial link between app functionality and security, ensuring that the final product is both user-friendly and safe.
QA engineers who also specialize in security are truly the hidden champions of mobile app creation, nailing down potential dangers way before the app even launches. These versatile pros don’t just look for crashes or awkward interface issues; they use advanced tools like MobSF to actively uncover weaknesses, such as insecure data storage or flimsy encryption, right from the get-go in the development process. By catching these problems early on, they save developers from the headache and expense of fixing things later, and they make sure your app runs smoothly while keeping everything safe and sound. You could say they’re the app’s guardians, ensuring it’s fantastic for users but a tough nut to crack for anyone trying to cause trouble.
Ethical Hackers and Mobile Penetration Testers
What Sets Them Apart:
- They adopt an adversarial perspective, replicating the strategies of actual attackers.
- They possess specialized knowledge in targeting mobile-specific weaknesses, such as the risks associated with jailbreaking.
- They leverage sophisticated tools like Burp Suite and Frida to conduct thorough penetration tests.
- They excel at uncovering hidden vulnerabilities that automated systems typically overlook.
Ethical hackers and mobile penetration testers are like digital defenders who put on the “bad guy” hat to keep your app secure. Armed with a toolkit and a hacker’s way of thinking, they dig deep into your app’s code, APIs, and how it runs, looking for any chinks in the armor, like endpoints that aren’t set up correctly or weak spots in how users log in. By staging realistic attacks, imagine jailbreaking an iPhone or messing with an Android app file, they uncover problems that could cause real trouble. The results they provide are incredibly valuable, giving developers a clear path to strengthen the app’s defenses and fend off would-be attackers.
Third-Party Mobile Security Firms
What Sets Them Apart:
- They offer an independent, unbiased viewpoint without being swayed by internal beliefs.
- They bring a wide range of knowledge from securing apps in many different industries.
- They conduct thorough audits that follow standards like the OWASP Mobile Top 10.
- They have access to the latest tools and methods for detailed testing.
When you need a powerful, objective partner, third-party mobile security firms step up to the plate. These specialized companies bring a fresh perspective, digging deep into your app with advanced static and dynamic analysis, penetration testing, and compliance checks. Because they’ve worked across various industries, they’ve encountered everything from unusual API weaknesses to cloud setup errors and they know exactly how to fix them. For apps that handle sensitive information, their meticulous audits are like a security deep-dive, uncovering hidden risks and making sure your app meets top-notch standards.
Bug Bounty Programs for Mobile Apps
What Sets Them Apart:
- A global network of security researchers providing a wide range of viewpoints.
- A budget-friendly, pay-for-results model that focuses on confirmed vulnerabilities.
- Ongoing testing that adjusts to new mobile threats.
- Specialized knowledge in areas such as Android/iOS-specific exploits.
Bug bounty programs tap into a worldwide community of ethical hackers to rigorously test your app, flipping the script on cybercriminals. Platforms like HackerOne and Bugcrowd link you with talented individuals who search for weaknesses, like insecure communication or code manipulation, in exchange for rewards. This crowd-sourced method brings together a variety of skills, revealing issues that internal teams might overlook. It’s as if you have a worldwide security team working around the clock to safeguard your app, all while keeping expenses tied to outcomes.
Automated Security Tools Managed by DevSecOps Teams
What Makes Them Stand Out:
- They offer scalable, high-speed testing that’s seamlessly woven into CI/CD pipelines.
- They provide continuous monitoring to spot vulnerabilities in both code and dependencies.
- They automate tedious tasks, letting humans tackle the trickier analysis work.
- They send real-time alerts for problems like outdated libraries or misconfigurations.
When DevSecOps teams put automated security tools to work, they become the cutting-edge protectors of mobile app security. By integrating tools like Snyk, Checkmarx, or QARK into development workflows, they can scan code, check dependencies, and watch how the app behaves in real-time, all at lightning speed. These tools catch issues, such as outdated libraries or insecure APIs, before they even make it to production, ensuring that apps can be released quickly without compromising safety. Imagine them as tireless guardians, working nonstop to keep your app secure while giving developers the freedom to focus on innovation.
How Mobile App Security Testing Is Performed?
Mobile app security testing is a really detailed process designed to find weaknesses and make sure your app is super secure against online threats. Every single step, from the initial planning all the way through fixing any issues, is super important for keeping user data safe, sticking to the rules, and building trust. We’ve got a breakdown of the specific steps below to give you a clear plan for locking down your mobile app.
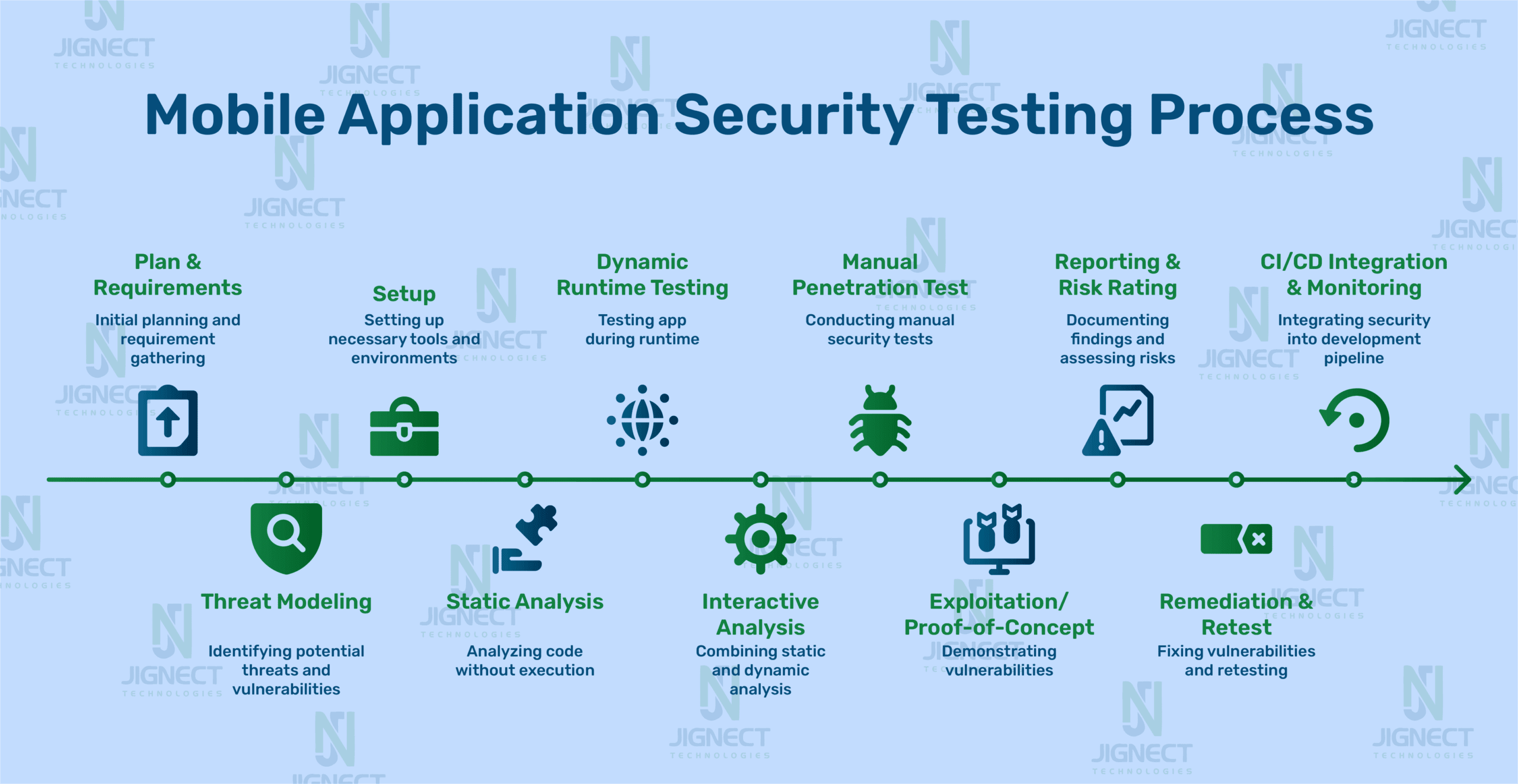
Step-by-Step Process
- Define Objectives and Scope
The First step is to Clearly describe the objectives of this security testing. it may include looking for vulnerabilities, ensuring compliance with GDPR or OWASP Mobile Top 10, or checking specific features such as payment systems. Define the scope of testing , including the app components (like frontend, backend, APIs etc.), platforms (like iOS, Android etc.), and environments (like staging, production etc.) to be included in testing. This step aligns all stakeholders and establishes expectations among all. - Collect Application Information 60 In this step, identify the architecture and data flow of the app, as well as its dependencies. Gather documentation, source code, and third-party code. Identify sensitive data (username, password, payment card information) to focus on during testing, as well as app-critical functionality (authentication method, API calls) to test.
- Threat Model the Application In this step, identify potential threats through the attack surface of the application. The attack surface includes points of entry; these may include an API, user input, and network connections, and you will need to perform a risk analysis of potential data theft, unauthorized access, etc. Create a threat model of the application and use this to prioritize identified vulnerabilities by likelihood and impact so you know where to focus your testing efforts.
- Setting Up Your Testing Space
Alright, before you go poking around for bugs, you need a little playground that won’t blow up your real stuff. Seriously, don’t mess with live data, nobody wants a “whoops, I wiped the database” moment. Get yourself a separate spot that’s basically a stunt double for your actual system. Fire up some emulators or simulators for iOS and Android, or, if you’re feeling fancy, use real devices. Toss in a bunch of versions and device types so you’re not just testing on your dusty old phone. Oh, and don’t forget your toolbox: MobSF, Burp Suite, Frida… all that good stuff. Make sure you actually have the app’s source code or at least the compiled app so you’re not just guessing. - Do Some Static App Security Testing (SAST)
Alright, time to get your hands dirty with the code, well ! not literally, but you get the idea. SAST is all about poking through your app’s source code or the binaries (without actually running the thing) to sniff out dumb mistakes like hardcoded passwords, sketchy APIs, or encryption that a toddler could crack. Honestly, tools like Checkmarx or SonarQube are lifesavers here. Catching these screw-ups early? Priceless. It’s like finding out you left your fly open before the big meeting. - Give Dynamic App Security Testing (DAST) a Spin
Now, instead of staring at lines of code, you get to see the app in action, sort of like watching someone drive your car to see if the wheels fall off. Fire up OWASP ZAP or something similar, and go nuts: try to break it. Look for stuff like weak session management, bad communication setups, or permissions that are way too generous. Toss in some MITM (man-in-the-middle) attacks for good measure and see if the app starts sweating. - Mix It Up with Interactive App Security Testing (IAST)
Here’s where it gets spicy. IAST is like having a security guard inside your app while it’s running, watching everything go down in real time. Plug in something like Contrast Security, and it’ll flag things like SQL injection attempts or insecure deserialization before you even finish your coffee. You get instant feedback, and it doesn’t cry wolf as much as other tools do. - Run a Software Composition Analysis (SCA)
If you’re using third-party libraries (and let’s be real, who isn’t?), SCA is non-negotiable. Tools like Snyk or Dependabot dig through your dependencies and point out which ones are ticking time bombs. Outdated modules, known vulnerabilities, maybe even some sketchy stuff snuck in there, SCA’s got your back. Update or swap out the junk before it blows up in your face. - Don’t Forget Secret Scanning
You’d be surprised how many people accidentally push their API keys or passwords to public repos. Oops. Secret scanning tools like TruffleHog or GitGuardian are like that nosy friend who catches your mistakes before anyone else does. They’ll sniff out sensitive info hiding in your code or configs so you can yank it out or toss it in a vault (think AWS Secrets Manager) where it actually belongs. Just do it, future you will thank you. - Conduct Manual Penetration Testing
Have some ethical hackers simulating real-world attacks looking to exploit vulnerabilities related to business logic, insecure authentication, jailbreaking, etc… They could use tools like Burp Suite or Frida to manipulate inputs, bypassing/potentially tampering with controls or code to discover issues that automated tools may not find. - Mess With the Business Logic and Authentication
Time to poke at the guts, try to break stuff like payment flows or user permissions. Can someone sneak into VIP features they shouldn’t? Push the login-OAuth, face unlock, whatever to see if you can smash your way in or hijack a session. Brute force it, try weird edge cases, get creative. The usual. - Go Platform-Specific, iOS and Android Quirks
Every platform’s got its own flavor of screw-ups. On iOS, people botch Keychain all the time. On Android? Intents get messy, fast. Check for jailbreak/root hacks, see if secure boot actually does anything. Fire up Drozer on Android, iOS Security Suite for Apple stuff… just dig for those “only-on-this-platform” bugs. - Smash the APIs
APIs love leaking data or letting you in where you don’t belong. Try broken auth, look for endpoints vomiting too much info, hammer them with requests, no rate limits? Yikes. Postman and Burp Suite are your best buds here. Chuck malformed, messed-up requests at every endpoint. If you can get past the locks, something’s busted. - Sniff the Network
Time to eavesdrop. Capture traffic with Wireshark or Charles Proxy, see if they’re sending stuff over plain HTTP (it happens more than you’d think). Any lame ciphers in use? Unencrypted data? That’s a big nope. Hunt for secrets flying through the air, shouldn’t be any, but you never know. - Look for Side-Channel Weirdness
Ever try to steal a PIN by watching the accelerometer? Yeah, it’s a thing. Check if the app leaks anything it shouldn’t through sensors or even power draw. Simulate some attacks, run scripts, see if you can get info you’re not supposed to. If the app’s letting every sensor run wild, that’s a red flag. - Write It All Down (For Real)
Don’t just keep this stuff in your head. List every bug, where it lives, how bad it is, what could go wrong. Use CVSS if you wanna be fancy with risk scores. Drop screenshots, PoCs, and clear steps on how to fix it. If a dev can’t follow your writeup, it’s basically useless. - Triage, Then Fix Stuff
Not all bugs are equal. Put the “oh crap” ones at the top. Team up with devs, patch the nastiest holes, nuke old libraries, whatever it takes. Give ‘em tips on writing safer code so you’re not doing this dance again next month. - Did It Actually Get Fixed? Prove It
Go back, run your tests again, double-check that everything’s locked down. Regression test, too, so the “fix” didn’t break something else. Don’t just trust automation testing; poke around manually to make sure. - Keep an Eye Out, Always
Security’s not a “one and done” thing. Set up monitoring RASP, SIEM, whatever your flavor, to catch new bugs as they pop up. Regular audits, push security checks into CI/CD, just keep the pressure on. Hackers don’t sleep, so neither can your protection. - Teach the Crew, Make Security Everyone’s Problem
Run workshops, send folks to OWASP trainings, whatever gets the team up to speed. Devs, QA, ops, everybody needs to care. Make security part of the culture, so it’s not just a checklist at the end, but something people think about all the way through. Otherwise? You’re just playing whack-a-mole forever.
Why even bother with all these steps? Simple cutting corners here is just asking for trouble. You wanna ship an app and sleep at night, right? This isn’t just about ticking boxes; it’s about making sure you didn’t miss some glaring hole that hackers will laugh at later. I mean, you’re not just checking code, you’re poking at everything: APIs, sensors, the weird stuff under the hood. If you skip a layer, congrats, you just handed over user data on a silver platter. And don’t even get me started on compliance. Bottom line: every step matters. Slack off and your app’s toast. Stay sharp and people actually trust what you build. That’s the whole game.
Security Testing Types for Mobile App
Think of your mobile app as the vault in a high-octane heist film, where hackers are hiding there like a band of outlaws planning their big score. Each kind of security test, automated, manual, or some crazy hybrid, is essentially an additional eccentric expert on your team, each with their own methods for securing the area before the criminals even approach. We’re not just talking about scanning a code and moving on. No, the goal of these tests is to outsmart the attackers and make your app the Fort Knox of the digital world. Now, let’s explore the realm of mobile security testing and discover how each approach adds a unique flavor to the work.
Manual Testing
Manual testing? That’s your classic gumshoe detective stuff. You’ve got real people poking around, sniffing out weirdness that automated tools would totally gloss over. It’s like having someone with a magnifying glass digging through your app’s dark corners, double-checking that your logic, permissions, and setups aren’t just wishful thinking.
Mobile Business Logic Testing
Why It Matters:
Think of it like spotting a smooth-talking scammer trying to sweet-talk your app out of freebies. Testers jump into your app’s main workflows, stuff like payments, user roles, all the juicy bits, and try to pull fast ones. Maybe they’ll see if they can skip paying for something, or get admin powers without earning them. Basically, they’re acting like sneaky users to make sure your app isn’t handing out the keys to the kingdom. For mobile, this is massive, if you screw up logic here, you’re just throwing money (and user trust) out the window.
Example:
Let’s say you’ve got an e-commerce app. Testers try to hack the checkout so they get a massive discount or stuff for free. If they pull it off? That’s a facepalm moment, so devs lock it down, no more loopholes, money stays where it belongs.
Authentication and Authorization Testing
Why It Matters:
Imagine someone rattling every lock on a bank vault, making sure only the right folks get in. That’s what this is. Testers try to break into login systems, passwords, fingerprint scans, you name it. They’re out here trying weak passwords, session hijacks, even poking at OAuth like it owes them money. For mobile, where people share devices or hop on sketchy Wi-Fi, this stuff’s critical. One slip and anyone could stroll in and trash your user’s trust.
Example:
In a banking app, testers go after MFA by intercepting session tokens over public Wi-Fi (yeah, that’s a thing). If they can snag access, devs have to up their game, think stronger tokens and extra layers of security.
Mobile Penetration Testing
Why It Matters:
This is basically hiring a professional thief to break into your app, just to see if they can. These folks use everything from off-the-shelf tools like Burp Suite to wildcards like Frida, trying to bust through your defenses. They’ll exploit bad APIs, check for jailbreak shenanigans, basically anything that’ll get them in. For mobile, it’s not just a checkbox, it’s how you find out if your app can take a punch.
Example:
On a social media app, testers use a sneaky API exploit to peek at private messages. That’s a giant red flag for privacy, so devs throw up tighter API checks, no more snooping allowed.
Configuration and Permissions Testing
Why It Matters:
Ever seen an app asking for way too much? Like, why do you need my location and my grandma’s birthday to take notes? Testers look for stuff like that, they poke around permissions and config settings, making sure you’re not leaving the doors wide open or running in debug mode by accident. People are already jumpy about privacy, so this step is all about building trust by only grabbing what you really need.
Example:
A note-taking app asks for microphone access for…no reason. Testers catch it, devs drop the permission, and suddenly users aren’t side-eyeing your app’s privacy settings. Trust: restored.
Automated Testing
Automated testing? Oh, it’s the superhero you didn’t know your app needed. Picture a bunch of cyber-bots zipping through your code at warp speed, ferreting out weak spots before anything goes kaboom. Like, you get to focus on the fun stuff, and these bots are just out there, kicking vulnerabilities in the teeth.
Mobile Security Scanners (MobSF, Drozer aka your digital bloodhounds)
Why It Matters?
It’s like some kind of digital sniffer dog, but way less slobber. MobSF, Drozer, these things rip through your Android or iOS app, hunting for things like sketchy permissions or sloppy data storage. They’ll poke at your binaries, flip through your configs, and spit out a list of “fix this before it bites you.” If you’re building a mobile app, honestly, these scanners are like having a panic button for platform-specific screw-ups.
Example:
Say you’ve got a fitness app. MobSF spots you’re storing workout logs in plain text, just lying around for any thief with a phone to grab. Encrypt that stuff, and suddenly, a stolen device isn’t a goldmine for creepers.
Static Application Security Testing (SAST) for Mobile
Why It Matters?
Think of SAST as X-ray goggles for code. It stares right through your source files (or even the binaries) and calls you out for dumb mistakes, like leaving your API keys chilling in plain sight or using encryption that a toddler could break. Catch this stuff before your app goes live, or good luck explaining to your boss why the servers are on fire.
Example:
Messaging app? SAST finds your API key hardcoded in there. Oops. Move it into a vault before some script kiddie finds it and starts poking your backend.
Dynamic Application Security Testing (DAST) for Mobile
Why It Matters?
DAST is like stress-testing your app with fake attacks. Imagine shooting missiles at your own fortress just to see what blows up. OWASP ZAP and friends will run your app, poke at its live features, and see if it leaks info over insecure channels or botches session handling. For anything money-related, like mobile banking, this is non-negotiable.
Example:
Your shiny new payment app? DAST catches it sending card details over HTTP. Bruh. Patch that before someone sniffs transactions at Starbucks.
Interactive Application Security Testing (IAST) for Mobile
Why It Matters?
This is basically James Bond embedded inside your app. IAST tools like Contrast Security hang out during runtime, flagging sketchy behavior from the inside, like objects being deserialized in ways that open the door for hackers. It’s real-time, super granular, and doesn’t slow your devs to a crawl.
Example:
Game devs: IAST spots cheaters tweaking the score mid-game. Fast patch, and you don’t have to watch your leaderboard turn into a circus.
Software Composition Analysis (SCA) for Mobile Dependencies
Why It Matters?
Ever check the ingredients before eating something weird? SCA does that for your app. Snyk and pals scan your third-party libs for old bugs or ugly vulnerabilities. Because, let’s be real, everyone’s using open-source, and nobody wants their app pwned through some crusty dependency.
Example:
E-learning app using a library from 2015? SCA flags it, you update, and bam, no more easy wins for hackers trying to sneak in through the backdoor.
Secret Scanning in Mobile Apps
Why It Matters?
Secret scanners are like treasure hunters, except they’re hunting for your embarrassing slip-ups, like passwords or keys you accidentally left in the code. TruffleHog and friends find those skeletons before someone else does.
Example:
Travel app with an API key just vibing in the code repo? Secret scanning finds it, you lock it up tight, and nobody’s hijacking your booking system.
Fuzz Testing for Mobile Apps
Why It Matters?
Fuzzing is basically playing dodgeball with your app, just chucking weird, broken inputs at it to see if anything explodes. AFL and similar tools go wild on your APIs or file parsers, catching bugs you’d never think to check for.
Example:
Video streaming app eats some glitchy metadata and faceplants. Fuzz testing exposes it, you fix the bug, and your users can binge in peace without random crashes.
Testing Approaches
Picking a testing approach for your app? To be honest, it’s similar to choosing your weapon for a zombie apocalypse; it depends on how you want to live (and look good doing it). Every technique has a distinct flavor, and if you want your app to withstand real-world nonsense, you kind of need to use them all.
Black Box Testing for Mobile
Why It Matters?
Picture yourself as a hacker with no cheat codes, just vibes, poking around, hoping to trip over something juicy. That’s black box testing. You don’t get to peek under the hood; you just mess with inputs, poke APIs, and spy on network traffic, trying to break stuff. It’s pure chaos energy, but it works, because it’s exactly how some random attacker on the internet would try to break your app.
Example: Let’s say you’ve built a food delivery app. Black box testing stumbles across an API that’s basically screaming user addresses out loud. Not good. You fix the API, and boom, suddenly nobody’s leaking dinner locations to creeps.
White Box Testing for Mobile
Why It Matters?
Now, flip it. You’ve got the source code, the keys, the whole dang blueprint. You’re not just poking at the doors, you’re checking for cracks in the foundation. With white box testing, you (or your testers) dig in deep, running static analysis, manual code reviews, all the nitty-gritty stuff. It’s OCD-level detail. Miss a hardcoded password? Not on your watch.
Example:
Think health app. White box testing finds out all those patient records are “protected” by the crypto equivalent of duct tape. That’s a lawsuit waiting to happen. So you beef up the encryption, and now everyone’s data is locked down, HIPAA-style.
Grey Box Testing for Mobile
Why It Matters?
This one’s in-between, like you’ve got a peek at the map, but you’re still mostly in the dark. Maybe you have some user credentials, maybe you scrounged an API doc from a dev. Grey box is about practical attacks: you know just enough to be dangerous. It’s perfect for sniffing out stuff like privilege escalation, where one wrong button gives you admin powers.
Example:
Take a ride-sharing app. Grey box testing uncovers a bug where drivers can somehow access admin controls. That’s a nightmare. Patch it up, and you stop drivers from going full “boss mode” on your system.
Listen…. No single method is the silver bullet. Real talk: if you want an app that doesn’t instantly fold under pressure, you gotta mix things up. Manual checks, automation, black/white/grey, all of it. By doing this, you can outsmart the game and find the strange bugs and cunning holes before some bored teen with a laptop does. Strong mobile security testing ultimately aims to create an app that users can genuinely trust, not just to check boxes. Instead of a cardboard cutout, you want a fortress. Thus, test frequently and intelligently to ward off zombies (or hackers, for that matter).
Common Mobile Application Vulnerabilities
Mobile apps handle sensitive data like passwords and payment details, making them prime targets for attackers. Vulnerabilities in these apps can lead to data breaches, financial loss, and damaged trust. Below, we explore the most common mobile app vulnerabilities, their risks, and how to address them, ensuring your app stays secure and users remain protected. We have also added few emerging risks that are gaining attention in 2025.
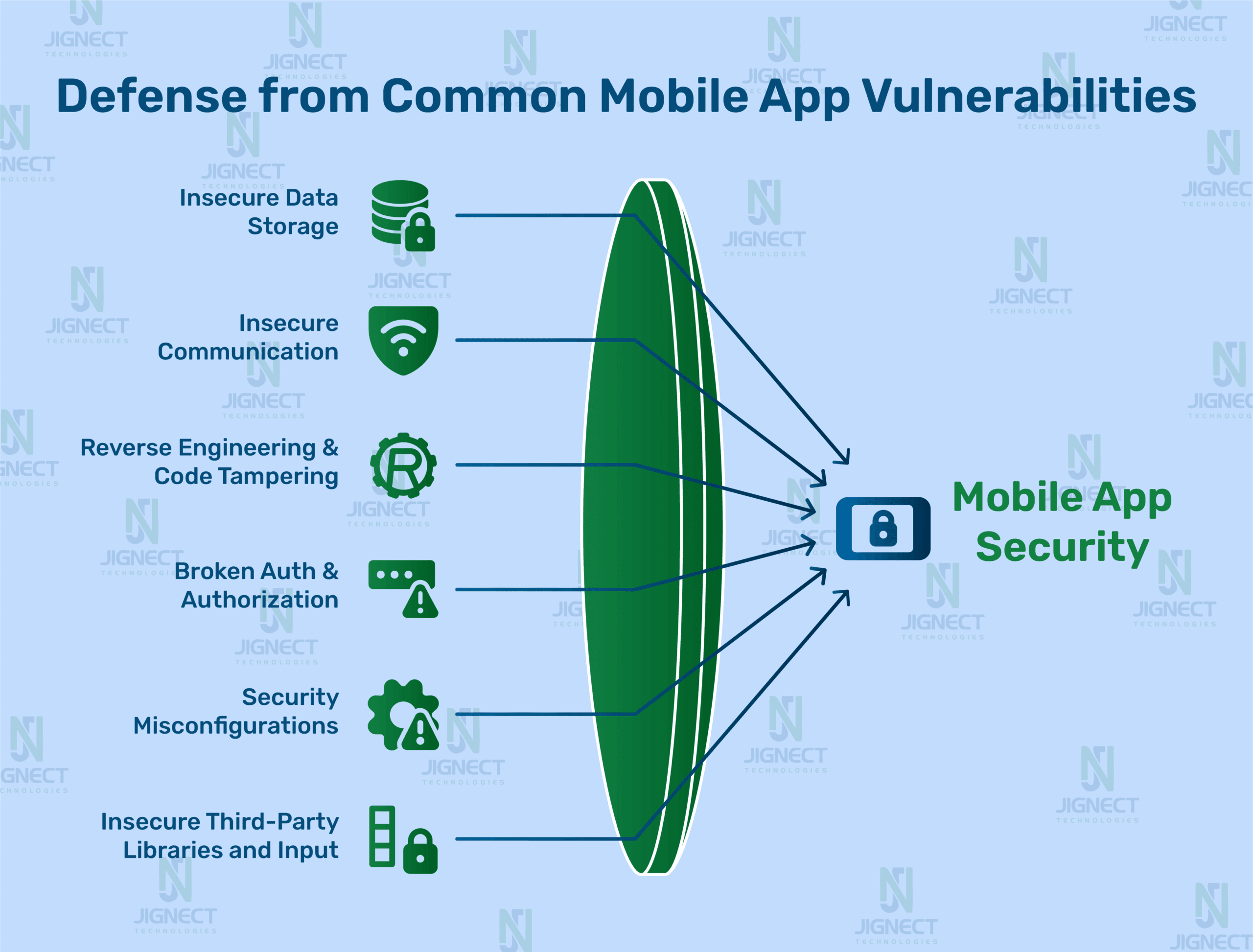
Insecure Data Storage
Storing sensitive data without proper protection leaves it open to attackers. Whether through stolen devices or malicious apps, insecure storage can expose user information, leading to privacy violations and financial harm.
- Local Storage Vulnerabilities
- Why It’s Critical:
Exposes data to anyone with device access!- Apps often save data like user credentials or session tokens in plain text files or shared preferences. Attackers with physical or remote access (via malware) can easily retrieve this data.
- Example:
A fitness app stored user location data in unencrypted files. Attackers accessed these files on rooted devices, tracking users’ movements and compromising privacy.
- Why It’s Critical:
- Unencrypted Databases
- Why It’s Critical:
Makes sensitive data readable to attackers!- Databases like SQLite are common in mobile apps. Without encryption, attackers can extract data like payment details or personal info if they access the database file.
- Example:
A banking app’s unencrypted SQLite database exposed account details when a device was compromised, leading to unauthorized transactions.
- Why It’s Critical:
- Improper Key Management
- Why It’s Critical:
Undermines encryption, rendering it useless!- Hardcoding encryption keys in the app or storing them insecurely allows attackers to decrypt protected data. Weak key generation further weakens security.
- Example:
A messaging app hardcoded its encryption key, enabling attackers to decrypt user chats after reverse-engineering the app.
- Why It’s Critical:
Prevention:
- Use platform-specific secure storage (e.g., iOS Keychain, Android Keystore).
- Encrypt data with AES-256 or similar strong algorithms.
- Minimize local data storage, favoring secure server-side solutions.
- Use tools like MobSF to detect storage flaws during testing.
Insecure Communication
Transmitting data over unsecured channels exposes it to interception. Insecure communication can compromise user credentials, financial details, and more, especially on public networks.
- Lack of TLS/SSL
- Why It’s Critical:
Sends data in plain text for all to see!- Without TLS/SSL, data travels unencrypted, allowing attackers to read or alter it. This is common in apps that skip secure protocols for speed.
- Example:
A shopping app sent credit card details over HTTP, letting attackers on public Wi-Fi steal payment information.
- Why It’s Critical:
- Weak Encryption Protocols
- Why It’s Critical:
Uses outdated security that’s easily cracked!- Relying on old protocols like SSLv3 instead of TLS 1.2 or 1.3 makes data vulnerable to decryption by attackers exploiting known flaws.
- Example:
A healthcare app used SSLv3, allowing attackers to decrypt patient data during transmission, violating privacy regulations.
- Why It’s Critical:
- Man-in-the-Middle (MITM) Attacks
- Why It’s Critical:
Lets attackers hijack your app’s conversations!- Attackers intercept data between the app and server, often on unsecured Wi-Fi, to steal credentials or manipulate transactions.
- Example:
A travel app’s weak certificate validation enabled MITM attacks, letting attackers alter booking details undetected.
- Why It’s Critical:
Prevention:
- Enforce TLS 1.2 or 1.3 with strong ciphers.
- Implement certificate pinning to validate server identity.
- Avoid insecure channels like SMS for sensitive data.
- Use tools like Wireshark to analyze network traffic during testing.
Reverse Engineering and Code Tampering
Attackers analyze or modify app code to bypass security, steal data, or unlock features. Mobile apps, running on user devices, are especially vulnerable to these attacks.
- Code Obfuscation Failures
- Why It’s Critical:
Makes your app an open book for hackers!- Without obfuscation, attackers can easily read decompiled code to understand logic or extract secrets. Weak obfuscation offers little protection.
- Example:
A gaming app’s poor obfuscation let attackers unlock premium features for free, causing revenue loss.
- Why It’s Critical:
- Binary Patching
- Why It’s Critical:
Changes your app’s core behavior!- Attackers modify the app’s binary to alter functionality, like disabling payment checks or injecting malicious code.
- Example:
A modified version of a streaming app bypassed subscription checks, distributed via third-party stores, harming revenue.
- Why It’s Critical:
- Runtime Manipulation
- Why It’s Critical:
Twists your app’s actions in real-time!- Using tools like Frida, attackers inject code during runtime to bypass security checks or manipulate data.
- Example:
A betting app was manipulated at runtime to alter odds, allowing attackers to place fraudulent bets.
- Why It’s Critical:
Prevention:
- Use obfuscation tools like ProGuard or SwiftShield (OWASP MASTG).
- Implement integrity checks to detect code changes.
- Detect rooted/jailbroken devices with libraries like RootBeer.
- Employ RASP for runtime protection.
Broken Authentication and Authorization
Flaws in verifying user identities or access rights let attackers impersonate users or access restricted features, compromising accounts and data.
- Weak Session Management
- Why It’s Critical:
Opens doors to account hijacking!- Poorly managed session tokens, like predictable or long-lived tokens, allow attackers to steal sessions and access accounts.
- Example:
A ride-sharing app’s predictable session tokens let attackers hijack user accounts, booking unauthorized rides.
- Why It’s Critical:
- Insecure OAuth Implementations
- Why It’s Critical:
Misuses trusted login systems!- Misconfigured OAuth flows can let attackers steal tokens or bypass authentication, granting unauthorized access.
- Example:
A social media app’s OAuth flaw allowed attackers to log in as users, posting malicious content.
- Why It’s Critical:
- Bypassing Authentication
- Why It’s Critical:
Skips your app’s security gates!- Weak password recovery or flawed login logic lets attackers bypass authentication, accessing accounts without credentials.
- Example:
A finance app’s weak password reset let attackers take over accounts by guessing security questions.
- Why It’s Critical:
Prevention:
- Use secure, randomized session tokens with short expiration.
- Validate OAuth configurations per best practices (OWASP Mobile Top 10).
- Enforce strong authentication (e.g., MFA) and robust password policies.
- Test authentication flows with tools like Burp Suite.
Security Misconfigurations
Incorrect settings in the app or its environment create exploitable weaknesses, often due to oversight or default configurations.
- Exposed Debug Information
- Why It’s Critical:
Hands attackers a roadmap to your app!- Enabled debug modes in production leak sensitive data like API keys or stack traces, aiding attackers.
- Example:
A news app’s debug logs exposed API keys, letting attackers access premium content for free.
- Why It’s Critical:
- Misconfigured Permissions
- Why It’s Critical:
Gives apps too much power!- Requesting unnecessary permissions (e.g., camera for a calculator) risks data exposure if exploited.
- Example:
A flashlight app requested location access, which attackers used to track users via a compromised version.
- Why It’s Critical:
- Insecure Cloud Integrations
- Why It’s Critical:
Leaves your cloud data wide open!- Poorly configured cloud services, like public S3 buckets, expose sensitive data or allow unauthorized access.
- Example:
A retail app’s misconfigured cloud bucket leaked customer addresses, leading to privacy violations.
- Why It’s Critical:
Prevention:
- Disable debug features in production builds.
- Request minimal permissions.
- Secure cloud configurations with access controls and encryption.
- Audit configurations with tools like CloudSploit.
Insecure Third-Party Libraries and SDKs
Using outdated or malicious libraries introduces vulnerabilities, as mobile apps often rely on open-source components.
- Outdated Library Risks
- Why It’s Critical:
Imports known flaws into your app!- Old libraries with unpatched vulnerabilities can be exploited to compromise the app or device.
- Example:
An e-learning app’s outdated library allowed attackers to inject malicious code, stealing user data.
- Why It’s Critical:
- Malicious Libraries
- Why It’s Critical:
Sneaks malware into your app!- Libraries with hidden malicious code can steal data or harm users, often from unverified sources.
- Example:
A photo-editing app’s malicious library sent user photos to a remote server, breaching privacy.
- Why It’s Critical:
- Dependency Vulnerabilities
- Why It’s Critical:
Weak links in your app’s chain!- Flaws in library dependencies can cascade, exposing the app to attacks like remote code execution.
- Example:
A music app’s vulnerable dependency enabled attackers to crash the app, disrupting service.
- Why It’s Critical:
Prevention:
- Monitor libraries with tools like Snyk.
- Vet library sources for trustworthiness.
- Update dependencies regularly to patch vulnerabilities.
- Use SCA during development to catch issues early.
Inadequate Input Validation
Failing to validate user inputs properly can lead to exploits, as mobile apps often process diverse inputs from users or external sources.
- Injection Attacks
- Why It’s Critical:
Lets attackers run malicious code!- Unvalidated inputs can lead to SQL injection or command execution, compromising data or functionality.
- Example:
A chat app’s unvalidated input allowed SQL injection, exposing user messages from the backend database.
- Why It’s Critical:
- Buffer Overflows
- Why It’s Critical:
Crashes or hijacks your app!- Poor input handling can overflow memory buffers, enabling attackers to execute arbitrary code.
- Example:
A video player app’s buffer overflow let attackers crash the app, disrupting user experience.
- Why It’s Critical:
Prevention:
- Sanitize and validate all inputs using secure APIs.
- Use parameterized queries to prevent injection.
- Implement fuzz testing to uncover input flaws.
- Follow OWASP input validation guidelines.
Staying ahead of these vulnerabilities requires a proactive, layered security approach, combining secure coding, regular testing, dependency management, and ongoing monitoring. As the mobile threat landscape evolves, so too must the strategies for defending against these common and emerging risks.
Mobile Device and Platform-Specific Security Considerations
Think of your mobile app as a traveler trying to get through a busy and unpredictable city. Each device or platform, like iOS or Android, acts like its own neighborhood with specific rules and potential dangers. If you overlook these differences, your app could be at risk leaving user data or app features open to threats. You need specific strategies to handle things like device fragmentation, platform APIs, jailbreaks, hardware security, biometrics, and notifications to keep users safe.
Take Zoom as an example. Back in 2019, its iOS app ran into trouble because it bypassed App Transport Security. By misconfiguring an API, the app sent data over unsecured networks, which could have put user privacy at risk. Read More on The Verge.
Developers build apps that succeed in the mobile world by tackling platform-specific needs. This helps them gain user trust and steer clear of expensive security issues.
Device Fragmentation Challenges
The mobile world includes a mix of devices with different hardware, operating systems, and setups. This variety makes security harder because apps need to work well on everything from low-cost Android phones to premium iPhones and other devices.
Android’s Open Ecosystem Variability
- Why It’s Critical?:
- The range of Android devices is huge. Apps must stay safe across all kinds of setups. If not weak spots might appear on less common models.
- Description:
- Android’s open-source setup lets makers modify hardware and software however they like. This leads to tons of different devices. Some security features like biometrics or encryption differ, and older versions might not have the latest protections. An app that works well on a Galaxy S23 might fall short on an older or lesser-known device using Android 9.
- Real-World Example:
- In 2025, older Android devices using Android 8.0 (Oreo) experienced crashes when running the UPI app BHIM. This happened because certain cryptographic libraries were not supported. These issues raised concerns about transaction data being exposed. The situation highlighted the importance of conducting wide-ranging compatibility tests within Android’s varied ecosystem (MediaNama, 2025, link).
- Best Practice:
- Use feature detection to adapt to device capabilities and test on diverse Android versions to ensure consistent security.
iOS Version and Hardware Differences
- Why It’s Critical?:
- Even in Apple’s controlled environment, variations in software versions and hardware can create security risks if overlooked.
- Description:
- iOS is consistent to an extent, but differences between versions like iOS 12 and iOS 18, or devices like an iPhone SE and an iPhone 16, can change how secure they are. Older systems might not include upgrades like Face ID or stronger encryption. Developers need to decide which minimum version they will support.
- Real-World Example:
- In 2018, the Lloyds banking app ran into problems on iOS versions older than 10. Outdated security setups caused login issues and left sessions open to risks. This situation pushed developers to release updates (LancsLive, 2025, link).
- Best Practice:
- Set a minimum iOS version with robust security features and test on older devices to confirm compatibility.
Testing Across Device Models
- Why It’s Critical?:
- Only broad testing catches security flaws unique to specific devices or OS configurations.
- Description:
- You need to test apps across multiple devices. This includes checking different models, operating system versions, and device states like rooted and non-rooted. Emulators can assist in testing, but physical devices uncover hardware-related problems. Automated tools speed up coverage, but manual testing ensures depth.
- Real-World Example:
- In 2020, WhatsApp ran into serious data leak risks on basic Android phones with low memory. Certain configurations that weren’t tested caused crashes and made chat data vulnerable. WhatsApp had to run extensive tests on devices to fix this issue (Times of India, 2020, link).
- Best Practice:
- Use both automated and hands-on testing on real devices to make sure all the mobile variations are tested.
Platform-Specific API Risks
Android and iOS have APIs that developers use to boost app capabilities, but improper use might lead to security issues. Features like Android’s inter-app communication and iOS’s secure storage need developers to handle them with care.
Android Intents and Permissions
- Why It’s Critical?:
- Weak permissions or leaky intents can let attackers grab sensitive info or even take over parts of a device.
- Description:
- Android’s intent system helps apps communicate but sometimes leaks data when apps use implicit intents. Malicious apps might catch these and steal things like payment info. Permissions, especially dangerous ones (e.g., camera), must be minimal and requested at runtime since Android 6.0.
- Real-World Example:
- A flaw in Android’s intent setup let bad apps snatch private data from major apps like Google Chrome in 2024. This happened because intent checking wasn’t done . It put user credentials and personal data at risk (The Hacker News, 2025, link).
- Best Practice:
- To stay safe always use explicit intents ask for what permissions you need, and check runtime permission results Android Intents.
iOS Keychain and App Transport Security
- Why It’s Critical?:
- Bypassing Keychain or ATS makes it harder for data protection and network security to work effectively.
- Description:
- The iOS Keychain is a secure place to store passwords and tokens and the App Transport Security (ATS) ensures that all connections are made via HTTPS. If ATS is disabled or Keychain settings are set to insecure, it is possible that a third party will intercept or steal the data without the knowledge of the parties. It is necessary to explain the reasons behind the exceptions given to the legacy servers.
- Real-World Example:
- TikTok’s iOS app was found to be bypassing ATS in 2020 and thus the user data were sent via unencrypted channels and therefore there was a possibility of interception. However, this situation lasted only until Apple imposed stricter ATS compliance regulations (Forbes, 2020, link).
- Best Practice:
- Sensitive data to be stored in the Keychain and try to keep ATS enabled without broad exceptions iOS Keychain.
Misuse of Platform Features
- Why It’s Critical?:
- Platform-specific features, if used in an improper way, can lead to the creation of weaknesses, which cybercriminals can take advantage of.
- Description:
- Android’s SharedPreferences or iOS’s NSUserDefaults are not secure for storing sensitive information, however, developers continue to misuse these. Using weak cryptography or being oblivious to the usage of platform guidelines (for example, Android’s Keystore, iOS’s Secure Enclave) can also lead to security being at risk.
- Real-World Example:
- Best Practice:
- Follow security guidelines specific to platform, using Keystore or Keychain for sensitive data OWASP MASTG.
Jailbreaking and Rooting Risks
Jailbreaking an iOS device or rooting an Android phone removes OS restrictions. This gives attackers a way to gain higher access, which puts app security at risk. These modified devices demand active detection and handling.
Detecting Jailbroken/Rooted Devices
- Why It’s Critical?:
- Catching modified devices helps apps reduce threats by blocking sensitive features.
- Description:
- Apps look for signs of jailbreaking like Cydia on iOS or rooting clues like the su binary on Android. When they find these, they act by turning off features like payments or warning users. Advanced attackers may bypass detection, so this method is not reliable.
- Real-World Example:
- Back in 2015, Netflix’s app on Android failed to block rooted devices. This flaw let people download unauthorized content. It forced Netflix to improve its root detection system (The Hacker News, 2015, link).
- Best Practice:
- Developers should look to use tools like RootBeer for Android or jailbreak detection solutions for iOS. However, they need to remember that these methods are not foolproof.
Security Implications of Modified OS
- Why It’s Critical?:
- A modified OS gives attackers ways to tamper with apps or steal sensitive information.
- Description:
- Devices that are jailbroken or rooted let attackers put in spying tools, change codes, or get into restricted files. This can result in stolen data unauthorized access to features, or using the device in botnets.
- Real-World Example:
- Back in 2015, the XcodeGhost malware targeted jailbroken iOS devices. It exploited OS changes to steal data from banking apps (BBC News, 2015, link).
- Best Practice:
- To reduce risk, avoid storing sensitive data and depend on server-side protections instead.
Mitigating Jailbreak/Root Exploits
- Why It’s Critical?:
- Building strong app structures limits harm even if detection does not work.
- Description:
- Apps need to go beyond just detecting issues. They should rely on server-side validations for essential functions like payments and avoid storing delicate data on the device itself. Adding techniques like Runtime Application Self-Protection or integrity checks helps find tampering and boosts security.
- Real-World Example:
- In 2017, Pokémon GO relied on server-side validation to stop fake scores on rooted Android devices. This step limited exploits even with root access (BGR , 2018, link).
- Best Practice:
- Use RASP along with server-side validation to reduce risks from modified operating systems.
Secure Boot and Hardware Security
Modern mobile gadgets include hardware-based tools like Trusted Execution Environments and secure key storage. These tools help boost security but need to be set up right and tested well.
Leveraging Trusted Execution Environments (TEE)
- Why It’s Critical?:
- TEEs shield critical processes keeping them safe from compromised systems.
- Description:
- Android has Keystore and iOS uses Secure Enclave to store keys and perform cryptographic tasks. These environments stay separated from the main OS. They protect sensitive data like biometrics and payment info even during OS breaches.
- Real-World Example:
- In 2016, Samsung Pay relied on TEE to stop data theft during a malware outbreak on Android. Other apps using software-based encryption were not as secure (The Indian Express, 2016, link).
- Best Practice:
- Complete all cryptographic tasks in TEEs Android Keystore.
Hardware-Backed Key Storage
- Why It’s Critical?:
- Storing keys in hardware makes them very tough to steal even if attacked.
- Description:
- Secure storage systems like Android’s Keystore or Apple’s Keychain rely on hardware like the Secure Enclave. This keeps keys safe from software breaches. Apps should choose these hardware systems instead of software storage.
- Real-World Example:
- In 2018, Coinbase’s iOS app used the Secure Enclave to guard crypto keys. This stopped theft during a phishing attempt, unlike apps that depended on software storage (CNET, 2018, link).
- Best Practice:
- Store cryptographic keys in hardware-supported storage.
Testing Hardware Security Integration
- Why It’s Critical?:
- Mistakes in integration take away the advantages of hardware security.
- Description:
- Developers need to confirm keys are in hardware, TEE operations work , and sensitive information is protected. This means running unit tests, doing integration testing, and even checking for weaknesses with penetration tests.
- Real-World Example:
- In 2017, some devices running Google’s Android Keystore had a problem. Weak TEE integration exposed keys, which they corrected after thorough testing, link).
- Best Practice:
- Use actual devices to ensure hardware security works .
Biometric Authentication
Using fingerprints or face recognition makes security easier to use but needs solid planning to avoid tricks or workarounds.
iOS Biometric Security (Touch ID, Face ID)
- Why It’s Critical?:
- Strong biometrics increase trust, but devices must rely on backup options.
- Description:
- Touch ID and Face ID on iOS rely on the Secure Enclave to manage sensitive data keeping it away from the main device. Apps must have a plan in case biometrics fail such as offering secure password access.
- Real-World Example:
- Back in 2016, HSBC, a banking app in the UK, had security issues with its Touch ID fallback. Hackers could use guessed PINs to get in without permission. After users spoke up, the problem was fixed (The Guardian, 2016, link).
- Best Practice:
- Implement biometric APIs that include secure fallback methods. iOS Biometrics.
Android Biometric Security (Fingerprint, Face Unlock)
- Why It’s Critical?:
- Android must ensure biometrics are strong enough to prevent vulnerabilities.
- Description:
- The BiometricPrompt API on Android manages fingerprint and face unlock features so biometric data remains under system control. Apps should provide safe backup options if biometrics fail or are unavailable.
- Real-World Example:
- In 2019, someone tricked the Galaxy S10’s fingerprint sensor using a 3D-printed fingerprint due to poor implementation. Samsung later fixed this issue with a software update (The Guardian, 2019, link).
- Best Practice:
- Use BiometricPrompt and ensure strong backup authentication methods Android Biometrics.
Secure Push Notifications
Push notifications remain a key feature of mobile apps, but poor handling can leak private info or allow unauthorized activities. This makes it important to implement them tailoring methods to each platform.
Android Notification Security
- Why It’s Critical?:
- Unencrypted notifications might reveal data on open Android systems.
- Description:
- Sensitive data like OTPs can appear on Android lock screens through notifications. Developers need to secure this by encrypting the content or using silent notifications to retrieve data in a safe way. Sideloading apps makes the use of signed notifications even more essential.
- Real-World Example:
- In 2020, a problem with Google’s Firebase Cloud Messaging allowed unencrypted push notifications to become visible. Apps such as banking apps were affected making OTP interception a potential risk (XDA Developers, 2020, link).
- Best Practice:
- Encrypt payloads when dealing with sensitive information. Use silent notifications as an additional precaution.
iOS Notification Security
- Why It’s Critical?:
- Public logs on iOS might reveal details from notifications if not secured.
- Description:
- Sensitive information can appear in iOS notifications, but public console logs may expose it. Using silent notifications helps reduce the need for storing data on servers while also protecting user privacy.
- Real-World Example:
- Back in 2018 Twitter’s iOS app recorded push notification details, like private DM previews, in public logs. This put user privacy at risk until it was fixed (Fortune, 2018, link).
- Best Practice:
- Send silent notifications instead and do not store sensitive information in logs iOS Notifications.
Why These Considerations Matter ?
Mobile devices play a big role in building user trust since they manage important tasks like making payments or tracking health. Risks come from things like fragmented devices, platform APIs altered operating systems, hardware security flaws, biometrics, and notifications. Developers who follow platform-specific practices and perform thorough testing can build apps that stay secure, meet standards, and remain trustworthy. This helps users feel confident even in a digital world full of threats.
Reporting and Remediation: Turning Mobile Security Findings into Action
Mobile apps carry private information such as health records and banking data so weak spots harm user trust . Turning these issues into solutions that are secure takes strong reporting and fixing. This part explains how to write solid reports, rank risks, work with developers, check fixes, and keep apps secure while threats keep changing.
Writing Effective Mobile Security Reports
Structure, Clarity, and Impact
Good reports play a big part in solving mobile security problems quickly. They connect testers and developers by breaking down complex issues into doable steps. A clear report makes risks easy to understand and provides straightforward solutions helping to avoid wasted time and expensive security failures.
How to Do It:
- Start with a template that includes an executive summary detailed results, and clear steps to fix the issues.
- Use plain language to make it easy to understand without relying on technical terms.
- Add visuals such as screenshots or diagrams showing how the attack works to make vulnerabilities clear.
- Group findings by specific components like Android intents or iOS Keychain to make the fixes more focused.
Prioritizing Mobile Findings
Some vulnerabilities are more dangerous than others, so it’s crucial to focus on the ones that pose the biggest problems. High-risk issues such as data leaks, can damage an app’s reputation badly. Smaller bugs though, can wait. Prioritizing fixes helps teams target the most significant threats and stay in line with business goals.
How to Do It:
- Use a risk matrix to sort issues by how likely and harmful they are, like the risk of financial loss.
- Tackle serious problems first such as exposed API keys, before worrying about less pressing stuff like UI bugs.
- Work with stakeholders to make sure priorities address key business risks, like avoiding compliance fines.
- Reassess priorities often because new threats and app updates can shift the risks around.
Communicating to Stakeholders
Getting stakeholders involved matters a lot when you need resources or solutions. Explaining technical risks in ways tied to business, like losing money or facing fines, helps. Working with both developers and leadership ensures everyone understands the priorities, which speeds up fixes and creates trust.
How to Do It:
- Adjust reports: give developers the technical details and show business leaders how the risks affect them.
- Use visuals like graphs or charts to make risk levels clear to those less familiar with tech.
- Point out consequences like possible GDPR penalties or customers leaving so management stays on board.
- Share regular updates about how fixes are going to keep stakeholders reassured.
Risk Rating and CVSS for Mobile
Severity Metrics for Mobile
Giving accurate ratings to vulnerabilities plays a key role in fixing them . Mobile apps come with their own set of challenges such as device variety or risks involving biometric data, which call for careful scoring. Teams can use common scales like CVSS to address the most severe risks first and safeguard both apps and users.
How to Do It:
- Apply CVSS v3.1 to score vulnerabilities based on exploitability and impact (0–10).
- Adjust scores for mobile factors, like widespread Android versions or data sensitivity.
- Document scoring rationale to ensure transparency and team agreement.
- Review scores periodically to reflect new threats or app changes.
Qualitative vs. Quantitative Ratings
Numbers alone don’t tell the full story, qualitative ratings add critical context. Sometimes a medium CVSS score can indicate a big business threat, like problems with privacy. Relying on both standard scoring and business context helps prioritize mobile risks with a balance of accuracy and practical consequences.
How to Do It:
- Pair CVSS scores with labels like “critical” or “low” for quick understanding.
- Factor in business risks, like regulatory fines or user trust loss, for qualitative ratings.
- Use team discussions to align quantitative and qualitative ratings.
- Document both ratings to justify prioritization to stakeholders.
Mobile-Specific Risk Factors
Mobile apps deal with unique challenges that standard metrics might overlook such as the broad range of Android devices or issues like jailbreaking. These elements can increase the effect of vulnerabilities when it involves sensitive data like biometrics or location. Accounting for them ensures ratings reflect the true threat to mobile users.
How to Do It:
- Assess risks from fragmentation, like older Android versions lacking updates.
- Focus first on problems with sensitive stuff, like fingerprints or payment information.
- Think about risks from jailbreaking or rooting that might get around app safeguards.
- Change risk factors as new mobile dangers or device habits show up.
Collaboration with Mobile Developers
Fixing and Validating Mobile Vulnerabilities
Collaboration with developers turns findings into secure code. Clear guidance and thorough validation ensure fixes work without introducing new issues. Strong teamwork catches vulnerabilities early, making apps safer and reducing future risks for mobile users.
How to Do It:
- Provide specific fix instructions, like using explicit intents for Android.
- Conduct code reviews to verify fixes align with security guidelines.
- Run penetration tests to confirm vulnerabilities are fully resolved.
- Document fix outcomes to track progress and prevent recurrence.
Fostering a Mobile Security Culture
A security-first mindset prevents vulnerabilities from the start. Teaching developers to approach problems like attackers helps create better apps with the tricky parts of mobile platforms. Adding security into the development process not avoids wasting time later but also keeps users safe from new risks.
How to Do It:
- Teach developers about the OWASP Mobile Top 10 and how to write code .
- Use threat modeling during development sprints to find issues on.
- Promote ongoing security talks to discuss the latest threats and ideas.
- Reward proactive security fixes to motivate the team.
Addressing Developer Resistance
Developers may push back on fixes due to tight deadlines or low perceived risk. Showing the real impact of vulnerabilities, like data breaches, overcomes resistance. Clear, practical solutions make security a team effort, ensuring faster and better fixes.
How to Do It:
- Demonstrate risks with attack scenarios, like session theft from a flaw.
- Offer quick, tested fix solutions to reduce developer workload.
- Involve developers in risk discussions to build understanding and trust.
- Highlight user or business impacts to align fixes with team goals.
Retesting After Fixes
Verifying Vulnerability Resolution
Retesting makes sure problems are resolved instead of being covered up. Skipping this step leaves apps open to the same attacks, which puts users’ trust and data at risk. Thorough verification confirms security and catches any new issues introduced during fixes.
How to Do It:
- Retest with original exploit methods to confirm vulnerability closure.
- Check for side effects, like new flaws from patching.
- Document retest results to track fix success and issues found.
- Involve developers to verify fixes align with code changes.
Mobile Regression Testing
Fixes can break app features, especially on diverse mobile devices. Regression testing ensures apps stay functional across Android and iOS versions, catching issues like crashes on older phones. It’s critical for delivering secure, reliable mobile experiences.
How to Do It:
- Test fixes across multiple OS versions, like Android 9 or iOS 12.
- Use device labs to cover varied hardware, like budget Android phones.
- Automate functional tests to speed up regression checks.
- Manually test critical features, like payments, for reliability.
Automated vs. Manual Retesting
Retesting needs both speed and precision to keep apps secure. Automated tools handle repetitive checks, while manual testing dives into complex mobile issues. Balancing both ensures thorough verification without slowing down development.
How to Do It:
- Use automated tools like Appium for repetitive API or UI tests.
- Manually test complex areas, like biometric authentication flows.
- Combine results to ensure comprehensive vulnerability checks.
- Schedule regular retests to catch issues in new app versions.
Monitor & Maintain Mobile Security
Continuous Monitoring for Mobile Apps
Mobile risks change every day aiming at apps with private information. Monitoring helps find security flaws quicker than hackers protecting the apps. It serves as the main defense in a world where mobile dangers keep shifting.
How to Do It:
- Deploy tools like MobSF to scan for new vulnerabilities in real time.
- Monitor app store feedback for signs of crashes or security issues.
- Set up alerts for suspicious activity, like unusual API calls.
- Review logs regularly to catch emerging threats early.
Patch Management for Mobile
Timely updates prevent hackers from taking advantage of known weaknesses. Testing and rolling out updates helps protect mobile apps on many devices and reduces the risk of breaches. Good patch management ensures apps stay strong without making things harder for users.
How to Do It:
- Focus on patches that address serious issues like API vulnerabilities or data exposure.
- Run tests on different devices to ensure patches work .
- Use automation to deploy updates faster and keep them consistent.
- Share patch information with users to keep their confidence intact.
Mobile Security Awareness Training
Well-informed teams and users play a big role in keeping mobile apps secure. When developers and users learn about risks like phishing or jailbreaking on, it reduces vulnerabilities right away. Keeping people aware over time creates a mindset focused on safety that helps protect apps in the long run.
How to Do It:
- Teach developers about secure coding and the OWASP Mobile Top 10.
- Show users how to stay safe, like by avoiding shady app sources.
- Refresh training each year to address new mobile risks.
- Share real-world examples of threats to make learning more interesting.
Best Practices: Incorporating Security into Your Mobile Applications
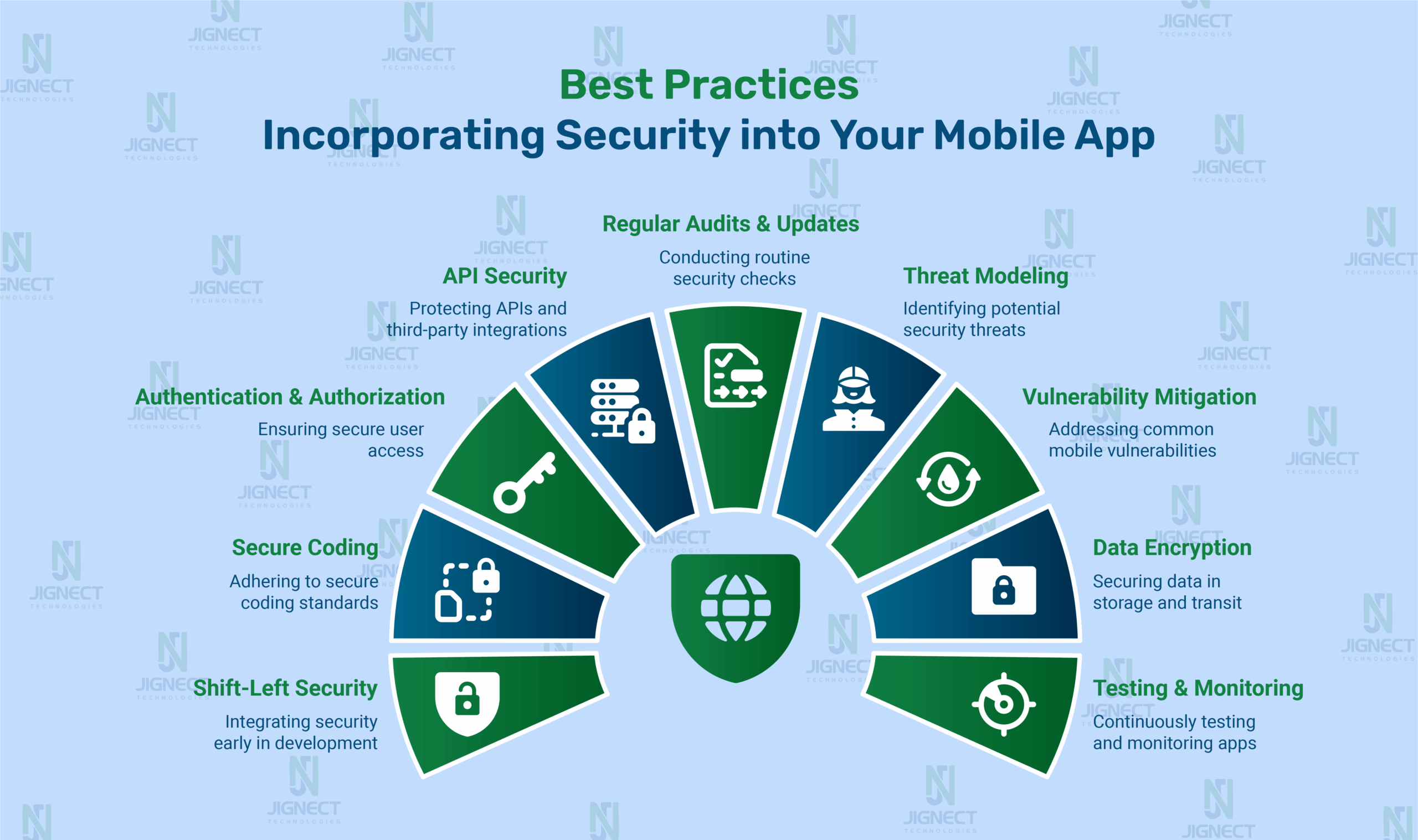
Mobile apps give users access to important things like medical records and bank info. Keeping these apps secure should always come first. Builders of these apps need to think about security right from the start of development and continue doing so during updates. This guide offers hands-on tips to protect apps from risks and keep them secure across many platforms and devices. These steps aim to help your team address possible weak spots and build stronger trust with users.
Implement Shift-Left Security in Mobile
Finding security issues can save time and protect users. Shift-left security focuses on adding protections as as the first line of code. It prevents issues before they happen instead of waiting until after a breach to fix them. This method keeps mobile apps safe whether they’re on Android’s wide system or iOS’s stricter setup.
How to Do It:
- Use security tools like static analyzers such as SonarQube while starting the development.
- Teach developers how to manage mobile-related risks when designing or writing code.
- Perform security scans within CI/CD pipelines to find issues before launching.
- Work closely with security teams during planning to focus on mobile threats.
Tools:
- SonarQube checks code in development to spot vulnerabilities.
- Checkmarx finds security issues in the code before it goes live.
- GitHub CodeQL pinpoints mobile-related problems in CI/CD processes.
Use Safe Coding Methods for Mobile
Safe coding forms the backbone of secure mobile apps. Every piece of code can be a risk if it’s not done right. Mobile platforms bring unique problems like sideloading and fragmentation. To defend user data and make apps reliable, planners must think about risks early and build protections from the ground up.
How to Do It:
- Use the OWASP Mobile Top 10 rules when coding for Android and iOS apps.
- Do not store sensitive information like API keys in your app’s code.
- Store important data using tools like Android Keystore or iOS Keychain.
- Check every user input to stop injection attacks such as SQL or XSS from happening.
Tools:
- MobSF (Mobile Security Framework) helps you detect mobile security weaknesses in your code.
- ESLint helps you apply safe coding rules for apps written in JavaScript.
- Veracode reviews and shows insecure code practices on multiple platforms.
Use Strong Login Security and Access Controls
Weak logins let attackers in. Strong protections like access controls and authentication ensure authorized people can use your app’s features or see its data. Tools like biometrics and role-based access play a big role in safeguarding private actions such as making payments on mobile apps. These methods stop unauthorized users and earn user trust.
How to Do It:
- Use multi-factor authentication like a password with a biometric option to protect risky features.
- Set up role-based access control to restrict user privileges.
- Use short-lived tokens and secure cookies to manage sessions.
- Test how authentication works on different devices to check compatibility.
Tools:
- Auth0 helps manage safe authentication and authorization processes.
- Okta adds multi-factor authentication to mobile applications.
- Firebase Authentication allows secure sign-ins across various platforms.
Keep Mobile APIs and Third-Party Connections Secure
Mobile apps rely on APIs and external services, but they risk security flaws without proper protection. An unencrypted API call can become a weak spot exposing user data. Locking down these connections keeps apps secure when they work across platforms or link with other services. Every interaction, whether inside or outside the app, needs to be safeguarded.
How to Do It:
- Apply HTTPS using strong TLS settings to secure API communication.
- Check and clean data shared with other services.
- Set up API authentication with OAuth 2.0 or API keys.
- Perform audits of third-party libraries to find known security issues.
Tools:
- Postman helps test and secure API endpoints as you develop them.
- OWASP ZAP checks APIs to find security problems.
- Snyk spots issues in third-party libraries.
Run Mobile Audits and Keep Everything Updated
Mobile apps change over time, and so do the risks tied to them. Performing regular audits helps find new weak points, while updates protect apps from fresh threats. Ignoring these actions can leave apps at risk on older iOS versions or Android devices with varied software. Taking action helps your app stay ahead of hackers.
How to Do It:
- Plan security checks every quarter using tools like MobSF or Burp Suite.
- Fix known vulnerabilities by updating libraries and app dependencies.
- Test updates on different devices to check both security and compatibility.
- Write down audit results to keep track of patterns and recurring problems.
Tools:
- Burp Suite helps with running security checks on mobile apps.
- MobSF is useful to find vulnerabilities during security audits.
- Dependabot sends alerts when dependencies become outdated and need updates.
Take Steps to Model Mobile Threats
Threat modeling works as a strategy to guard against attackers. It helps spot risks unique to mobile apps such as jailbreaking or unsafe notifications on. This step helps developers add security during the building process keeping users protected across various platforms. Think of it as a guide to creating a more secure app.
How to Do It:
- Map how your app’s data moves to find spots attackers could target such as APIs or stored data.
- Focus on the most likely and serious threats, like data exposure on rooted phones.
- Get developers and testers involved to model threats while designing the app.
- Update these threat models every time the app gets a new release to handle fresh vulnerabilities.
Tools:
- Microsoft Threat Modeling Tool makes it easier to see mobile app threats.
- OWASP Threat Dragon helps with building threat models specific to mobile apps.
- Draw.io is handy to map out data flow for analyzing threats.
Reduce Common Mobile Security Risks
Mobile apps deal with specific dangers like unsafe storage and exposed intents. Addressing common flaws prevents data breaches that may expose user details or damage devices. Knowing how attackers take advantage of vulnerabilities is key to securing your app. Securing your app allows it to stay protected and keeps users safe.
How to Do It:
- Use specific explicit intents instead of general implicit ones to secure Android intents.
- Employ runtime checks to detect jailbreaking or rooting on devices.
- Do not store sensitive data in insecure places like SharedPreferences.
- Fix issues from OWASP Mobile Top 10 on a regular basis.
Tools:
- Drozer helps test Android apps to spot intent-related vulnerabilities.
- Frida identifies when jailbreaking or rooting occurs during runtime.
- QARK finds issues like unsafe storage in mobile apps.
Encrypt Mobile Data at Rest and in Transit
Attackers see unencrypted data as a treasure trove. To protect user details stored on devices or shared through networks, Android and iOS rely on encryption. It acts like a shield guarding sensitive information such as passwords and health records from being exposed. Strong encryption creates a foundation of trust that cannot be broken.
How to Do It:
- Apply AES-256 to encrypt data saved on devices.
- Require HTTPS using TLS 1.3 for all communication over the network.
- Keep keys in secure hardware storage such as Android Keystore or iOS Secure Enclave.
- Use tools to test encryption strength on a regular basis.
Tools:
- OpenSSL helps with creating and managing encryption keys for mobile applications.
- Keychain Access on iOS keeps keys safe in the Secure Enclave.
- Android Studio helps set up Keystore for storing encryption keys.
Test and Monitor Mobile Apps Periodically
Your app’s safety relies on testing and monitoring working as constant watchdogs. Running tests often helps find weak spots . Monitoring helps detect live threats like API issues. Staying alert keeps your app safe on all kinds of devices and against new attack tactics. This approach protects user trust.
How to Do It:
- Perform regular penetration tests to find any new weak spots.
- Apply tools like RASP to keep an eye on how apps behave during runtime.
- Check functionality on both Android and iOS even on older devices.
- Look at app store reviews to spot problems like crashes or security risks.
Tools:
- Appium helps automate testing of mobile apps across different systems.
- RASP (Runtime Application Self-Protection) keeps track of app activity in real time.
- Nessus detects vulnerabilities when running scheduled tests.
Mobile Security Testing Standards & Guidelines
Mobile apps handle private information such as financial details and personal data. They need tough security measures to keep users safe and follow required rules. Guidelines from frameworks like OWASP, NIST, and ISO 27001 provide tested methods to make apps stronger against new security risks. This section helps your team learn ways to meet these standards and create secure mobile apps. Explore these tips to develop apps that people can trust and that resist threats.
OWASP Mobile Top 10
The OWASP Mobile Top 10 offers a crucial resource to identify and fix the most serious mobile app security issues in 2024. Hackers often aim at weak spots like insecure authentication on Android and iOS. Developers and testers should follow these tips to prevent breaches and protect user data. This guide explains each of the ten risks so apps can have stronger security measures.
Key Mobile Vulnerabilities and Mitigations
- M1: Improper Credential Usage
Stored or mismanaged credentials leave apps open to unauthorized access. Hackers pull keys or tokens straight from the code putting sensitive user data at risk. To counter this, use protected storage methods and validate credentials through servers. - M2: Weak Supply Chain Protection
Using unsecured third-party libraries and components brings risks such as dependency hijacking. Ignoring these problems can threaten whole apps. To protect systems, you need to review and update dependencies. - M3: Faulty Authentication or Authorization
Attackers bypass security barriers when authentication is poor or authorization lacks strength. They may access accounts or perform restricted actions without permission. Strong authentication systems and server-side checks help avoid such breaches. - M4: Insufficient Input/Output Validation
Weak validation lets injection attacks like SQL injection or XSS happen putting data at risk. checked inputs or outputs can trigger dangerous security breaches. To avoid exploits validate and clean all data. - M5: Insecure Communication
Sending unencrypted data makes private information easy to intercept. Poor TLS configurations give attackers a way to tamper with or read data. Always use HTTPS with strong TLS settings and do certificate pinning. - M6: Inadequate Privacy Controls
Weak privacy protections may leak or track data without consent. This damages user trust and could break privacy laws like GDPR. To keep data safe, collect what is needed and design systems with privacy in mind from the start. - M7: Insufficient Cryptography
Weak or old encryption methods make it harder to protect sensitive data and leave systems open to attack. Apps that still use outdated algorithms like MD5 remain vulnerable to threats. Use stronger options like AES-256 and ensure secure storage of encryption keys. - M8: Security Misconfiguration
Mistakes like failing to secure APIs or not changing default credentials create opportunities for attackers to break in. These errors make systems accessible without permission. Strengthen configurations and turn off unnecessary features before releasing to production. - M9: Insufficient Binary Protection
Skipping binary protection makes apps vulnerable to reverse engineering or tampering. Attackers target apps without proper protection to steal data or alter how they work. Adding obfuscation and runtime checks protects binaries from such risks. - M10: Extraneous Functionality
Sneaky features such as debug tools can let unauthorized users access apps. Hackers may abuse these unnoticed functions when the app goes live. Clean out unused code and check for hidden entry points before launching the app.
Prioritizing OWASP Mobile Risks
Not every OWASP risk is urgent. Paying attention to severe threats like data leaks instead of small problems helps focus on what matters. This method ties security testing to business goals, like preventing breaches or avoiding penalties, and lets your team deal with the biggest dangers.
How to Do It:
- Sort OWASP risks based on how hackers could exploit them and what impact they have on user safety or data protection.
- Use a risk matrix to decide which issues like weak communication methods need attention first.
- Match these priorities with how much they affect business needs such as following legal rules.
- Look at risks again whenever an app gets updated or when OWASP makes changes.
Training Teams on OWASP Mobile
Trained teams can catch problems on. To recognize risks early, developers and testers should study the OWASP Mobile Top 10. This knowledge builds a security-first approach, which plays a key role in creating safer apps. Regular training ensures teams can handle evolving mobile security threats.
How to Do It:
- Organize workshops to explain OWASP Mobile Top 10 to developers and testers.
- Offer training with real-life examples to teach fixes like secure coding methods.
- Plan sessions every year to go over OWASP updates and highlight new threats.
- Encourage team members to earn OWASP Mobile Security Testing certifications to build skills.
NIST Mobile Security Guidelines
Procedures and Controls for Testing Mobile Security
NIST guidelines give a clear plan to secure mobile apps by highlighting steps like encryption and access control to stop threats such as malware. Sticking to NIST rules helps meet industry standards and builds trust among users. Think of it as your roadmap to test mobile apps and follow the rules.
How to Do It:
- Apply NIST SP 800-53 rules such as limiting app access.
- Run tests that follow a standard process to check how well apps handle authentication and protect data.
- Write down the test results to prove the app meets NIST standards.
- Test these rules on both Android and iOS devices to maintain strong security.
Mobile Risk Assessment Processes
NIST’s risk assessment framework helps identify mobile threats . It checks for risks such as outdated software or unauthorized access and helps create plans to reduce these problems. This keeps mobile apps secure and aligned with safety rules.
How to Do It:
- Use NIST SP 800-30 to examine risks in mobile setups.
- Spot mobile risks like an old operating system or tampered devices.
- Tackle issues based on how serious and impactful the risk is.
- Review risk assessments with every app update or when new threats pop up.
Planning for Mobile Incident Responses
A good incident response plan reduces damage from mobile security breaches. The NIST guidelines explain steps to detect issues, respond , and recover from problems like data leaks. Careful planning makes fast responses possible, shields users, and ensures compliance. This plan acts as a safety net in a mobile security crisis.
How to Do It:
- Create a mobile response plan using NIST SP 800-61.
- Teach teams how to identify and handle issues like API vulnerabilities.
- Run drills to test how prepared your response plans are.
- Keep plans updated to address new risks or app changes.
CWE/SANS Top 25 for Mobile
Critical Mobile Software Errors
The CWE/SANS Top 25 lists coding mistakes such as not validating input , which can cause mobile security issues. Developers can stop these flaws to protect user information and devices from being at risk. This standard helps developers create more secure code. It plays an important role in making mobile apps safer.
How to Do It:
- Look through the CWE/SANS Top 25 to spot mistakes such as buffer overflows.
- Use secure coding methods to address the mentioned issues.
- Check apps during development to find vulnerabilities from the Top 25 list.
- Focus on fixing flaws that affect user data or app performance.
Static Analysis for Mobile CWE
Static analysis identifies coding mistakes , before apps go live. Addressing issues like weak encryption from the CWE/SANS Top 25 list helps mobile apps avoid serious vulnerabilities. Taking this step boosts the reliability of apps across different platforms. It plays a key role in creating secure mobile software.
How to Do It:
- Use static analysis tools to find CWE errors in mobile codebases.
- Pay attention to risky issues such as insecure deserialization or broken validation.
- Add static analysis into CI/CD workflows to catch problems.
- Work with developers to review results and fix priority issues.
Best Practices in Mobile Error Handling
Weak error management can leave apps open to attacks. For instance, exceptions might reveal sensitive data. The CWE/SANS guidelines emphasize strong error handling to safeguard mobile applications. Controlling errors prevents exposing private information, which is vital to keep apps secure and reliable.
How to Do It:
- Add try-catch blocks to handle exceptions in mobile apps.
- Do not include sensitive information in error logs or messages.
- Simulate attack scenarios such as invalid inputs, to evaluate error handling.
- Store error logs to protect user privacy and data.
PCI-DSS for Mobile Payment Apps
Security Checklist for Mobile Payments
PCI-DSS sets rules to keep cardholder data safe in mobile payment apps. It has a checklist that includes encryption, authentication, and access restrictions to keep transactions secure. Following these rules helps prevent data theft and fines while increasing trust from users. It acts as the standard to make mobile payments secure.
How to Do It:
- Use PCI-DSS guidelines to encrypt payment information with strong security methods.
- Set up secure ways to verify users for every payment transaction.
- Limit who can access cardholder data using role-based permissions.
- Keep records of compliance based on the PCI-DSS checklist to show during audits.
Mobile Vulnerability Management
Stopping vulnerabilities in payment apps protects financial data from being compromised. PCI-DSS outlines that apps must undergo constant scans and updates to fix risks like weak APIs. Doing this ensures apps remain safe and meet compliance on all devices. This is vital to safeguard transactions and maintain trust.
How to Do It:
- Run regular scans to catch vulnerabilities in mobile payment apps.
- Fix issues such as poor authentication methods.
- Check if patches work on both Android and iOS.
- Keep a log to track vulnerabilities and meet PCI-DSS requirements.
Mobile Security with Third-Party Vendors
Third-party vendors bring risks to payment apps through things like unsafe APIs. The PCI-DSS guidelines demand checking vendors to keep data protected and ensure compliance. Strong integrations block breaches that come from outside providers. This is needed to create a secure mobile payment system.
How to Do It:
- Check vendors’ PCI-DSS compliance before connecting them.
- Require vendors to use secure APIs with authentication methods such as OAuth 2.0.
- Keep a close eye on vendor services to catch security issues or data leaks.
- Make sure vendors follow PCI-DSS rules by including this in contracts.
ISO 27001 To Manage Mobile Security
Using ISO 27001 Controls To Secure Mobile
ISO 27001 gives businesses a strong structure to handle mobile security in an organized way. Key measures such as managing access and encrypting data, help safeguard apps against risks on different platforms. Putting these practices into action builds compliance and solid security. It serves as the base to create a secure mobile environment.
How to Do It:
- Use ISO 27001 controls like A.12.4 to monitor mobile app security.
- Restrict data exposure in apps by applying strict access controls.
- Follow ISO 27001 guidelines to encrypt sensitive information.
- Record the control applications to meet audit requirements.
Checking Mobile ISMS Compliance
Auditing checks if your mobile Information Security Management System (ISMS) follows ISO 27001 requirements. It confirms that controls like encryption work well on devices to keep compliance. These audits spot weaknesses in mobile security. They help build trust with users and get certifications.
How to Do It:
- Do yearly ISO 27001 audits to check your mobile app’s security measures.
- See whether your system handles mobile risks, like fragmented devices.
- Write down the audit results and create plans to fix issues for certification.
- Hire qualified auditors to assess how well your ISMS works.
Continuous Changes To Improve Mobile Security
ISO 27001 helps improve and protect mobile security. It strengthens the system by refining processes and controls to tackle threats like rooting or API attacks. This ensures apps stay secure and meet compliance over time. It is a smart way to safeguard mobile security for the future.
How to Do It:
- Adjust mobile security measures to respond to the latest threats.
- Use audits to strengthen ISMS procedures and protections.
- Teach teams about new risks in mobile security to build stronger defenses.
- Keep up with industry changes to follow ISO 27001 recommendations.
Conclusion
Mobile app security testing has become a central task. Everyone creating, managing, or launching mobile apps now needs to take it . With mobile apps offering more features and becoming more complex, the opportunities for attacks also grow. Problems can arise at any point, from improper permission settings to risky third-party libraries or jailbroken devices. Security testing aims not to catch weak spots but also to maintain trust, protect a company’s name, and keep the data that powers our mobile-driven world safe.
This guide has shown that keeping mobile security strong isn’t something you do once. It’s a never-ending process that involves testing working together across teams, and staying updated on both technical risks and user-related issues. To strengthen security over time, you can line up your methods with industry rules, build security into your workflows, and treat every weak spot as a way to get better.
We hope this detailed look at mobile app security testing has given you the tools you need to act. The best moment to secure your app has already passed, but your next chance is right now.
If you’ve enjoyed diving into mobile app security, here’s your chance to complete the picture. We’ve also created an in‑depth guide on Web Application Security Testing, covering common threats, proven testing approaches, and real‑world lessons you can put into practice.
Read the full Blog here: Web Application Security Testing: The Ultimate Guide to Protecting Web Apps
Witness how our meticulous approach and cutting-edge solutions elevated quality and performance to new heights. Begin your journey into the world of software testing excellence. To know more refer to Tools & Technologies & QA Services.
If you would like to learn more about the awesome services we provide, be sure to reach out.
Happy Testing 🙂